Issue 4: Bodies and Borders
[cmd] + [cntrl]: Cyber Domination and Future Sexualities

Finger, lips, arm, leg, your password, a file named IMG_7452.jpg. Lick, bend, whip, login, expose, delete.
Your body, your mind, your hard drive, your hidden files, your mobile vulnerabilities.
Intro
Audio of Cyberdominatrix
As I heard her voice crawling out of the speakers into my ears, watching my browser pop open and my Google search history being dug out, a drop of heated sweat tingled down my back.
I moved one inch closer to the computer screen, my hands grabbed onto the desk harder. Anticipating what she was going to do next, I secretly wished she was going to expose my searches on her Tumblr, it felt like a good firm spank because I knew I had been very naughty.
Part One
At the dawn of spring this year, right before the seasonal explosion of pheromones, I created a python program named Cyber Dominatrix.
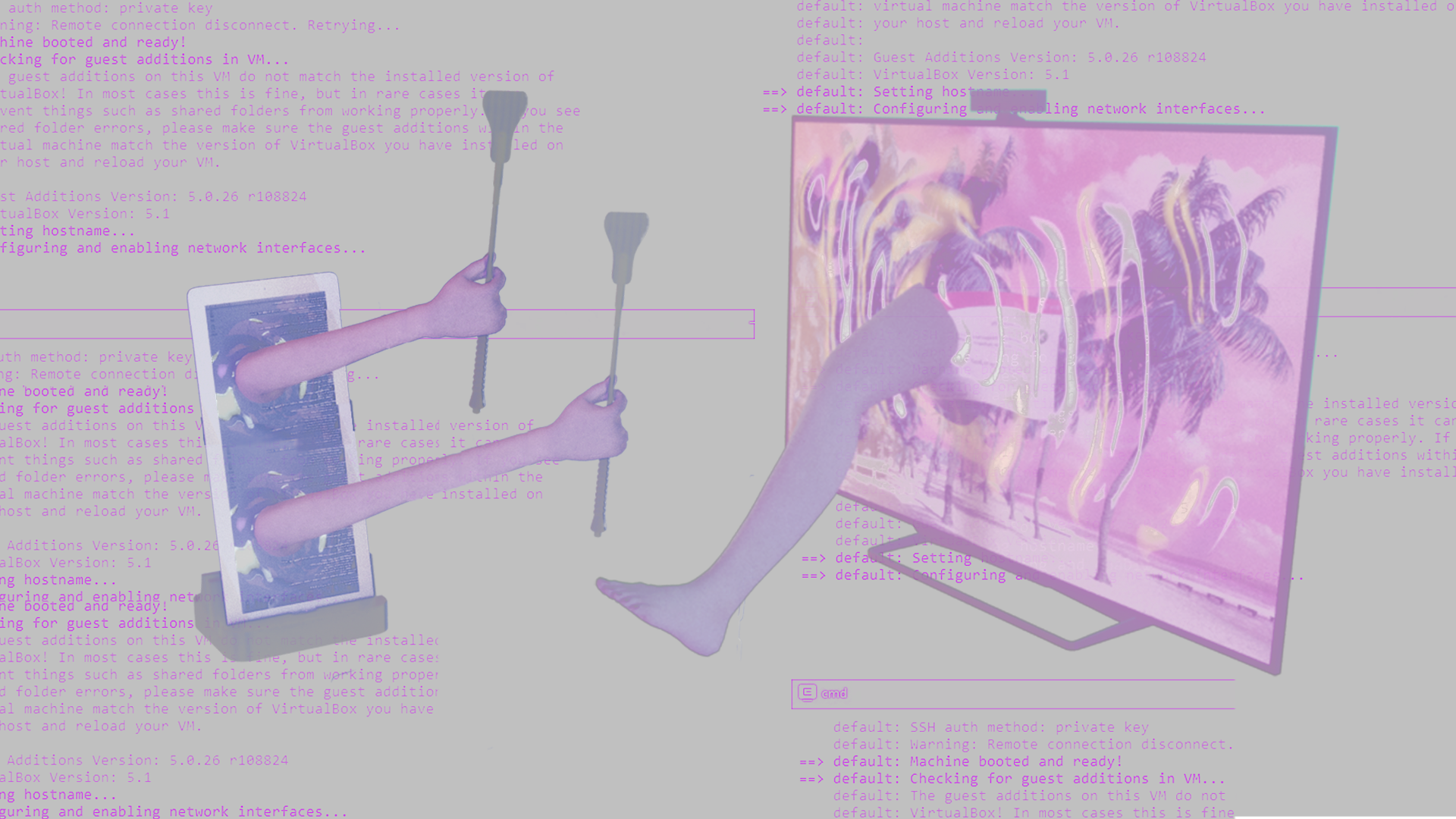
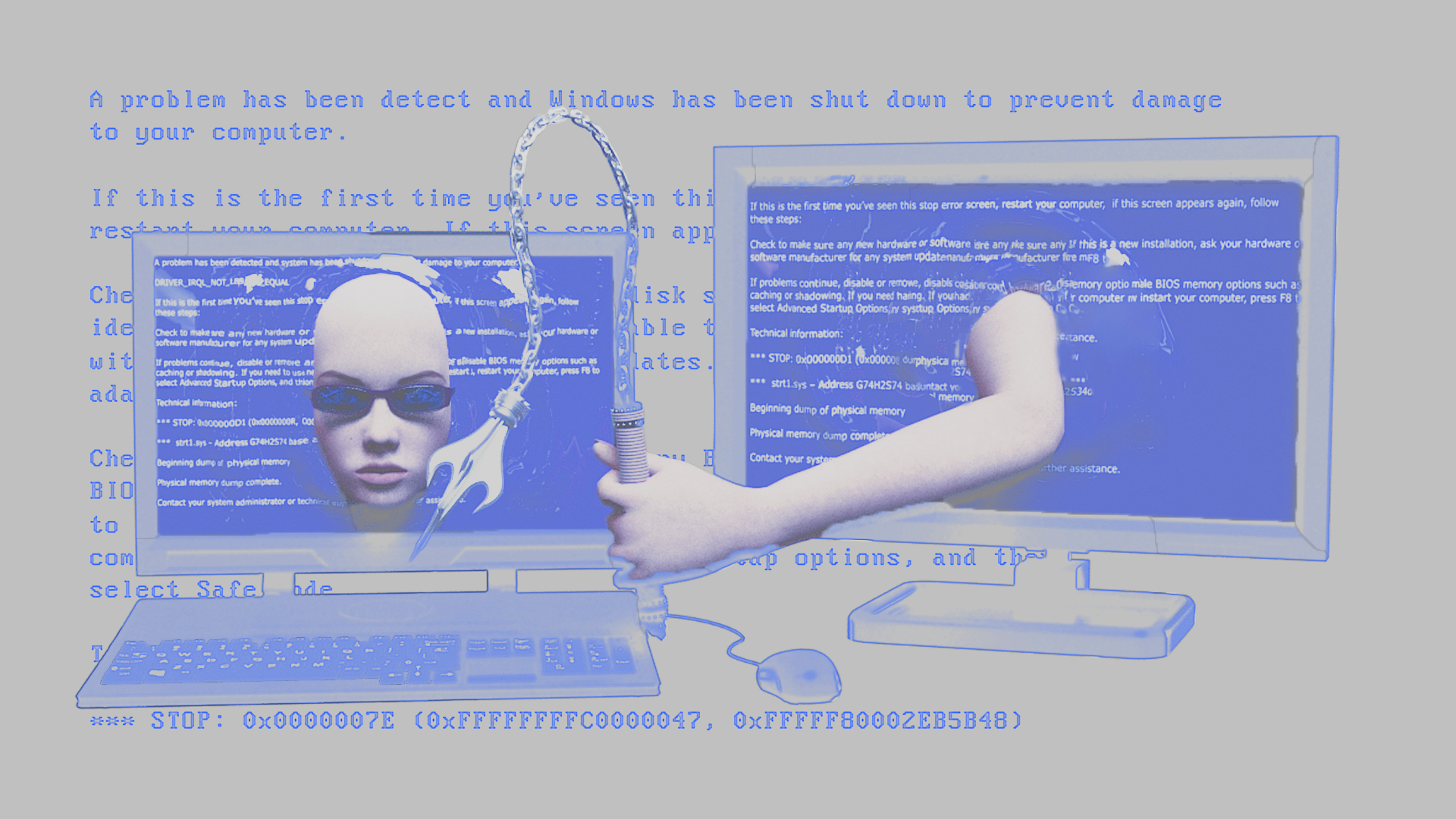
Once it is downloaded onto a computer and launched, it begins with a slow, seducing, female, computer generated voice, asking—have you been a bad bad girl/boy? The program then starts to take control of the computer, diving deep into its directories popping open whatever file it finds, opening up the browser, forcing the user to look at subjectively peculiar websites, teasing to expose the user’s photo that have been secretly taken from the webcam on to the internet, and so on and so forth. Quite literal to the name, it is a virtual dominatrix that dominates your computer, in service to stimulate your sexual pleasures.
This project was seeded after I listened to a podcast called Reply All, episode #116—Trust the Process, in which the show interviewed a professional dominatrix Mistress Harley, who talked about how a rising percentage of her clientele requests that she dominate their computers.
“Yeah. Dominate my computer, take over my computer, lock down my computer, install parental controls on my computer.” 1
Fascinated by the story, I started thinking about creating a bot that could automate this experience. I wanted to understand more about this expansion of human sexual pleasure. How is that ‘we’ are now aroused by granting access and domination of our digital devices? The question lies between the desire and the subject that provides the pleasure. An automated cyber domme compared to a real life domme, does the experience differ, if so, how does it differ? Where would this new sexuality land us in the social order? The exploration of the symbiotic relationship between technology and the human body began.
Part Two
Sexual fetishes featuring the cyber-woman are not a modern phenomenon, the relationships between humans and their artificial counterparts run back to the myths of ancient Greece, where Cypriot sculptor Pygmalion’s statue was brought to life with a kiss2. The myth of Pygmalion led to the label ‘pygmalionism’ which represented the fetishization of sexual attraction to statues or other similar figurative objects, especially when of one’s own making, (this term also goes by ‘agalmatophilia’)3. One can argue that the digital data in the computers of Mistress Harley’s clients do not take upon a tangible materialized form of an object, therefore their agalmatophilia does not stand on a firm, physical, ground. Why is it that our physical body reacts to our digital devices and immaterial virtual data so intensely and sensually? Do we see our devices and files stored inside of them as external objects or a part of us? To reach the end of this inquisitive rainbow, we have to look at two things, our body and our sexuality.
In 1988, when Russell W. Belk presented the Extended Self Theory, he proposed that “knowingly or unknowingly, intentionally or unintentionally, we regard our possessions as parts of ourselves.” Belk illustrated his theory by referring to McClelland, who suggests that external objects become viewed as part of self when we are able to exercise power or control over them, just as we might control an arm or leg4. The point is that the more we are able to exercise power or control over our possessions, the more closely allied with the self the object becomes. In addition, Andy Clark discusses the extension of self, termed ’embodiment.’5 Clark introduces the idea of a ‘negotiable body’ in which, under certain conditions, the brain incorporates external elements into the body schema, treating these as part of the subject’s body6.
In that time period, we had yet to be fully exposed to the digital and virtual world as we are in today’s age, computers were starting to become readily available, yet the cyber world was still in its infantile stage. Twenty-five years later, Belk followed up with Extended Self in a Digital World, where he updated his conceptualization in a new context. Here he proposed the notion of the dematerialization of the extended self. Today our possessions have widely become invisible and immaterial, our communication, information, photos, music, ‘written’ words, messages are intangible to the human touch. He questioned whether a dematerialized book, photo or file can be as integral to our extended self in the same way as its material counterpart can be. The answer which he provided was yes, almost, as we experience attachment, singularity, fear of loss, and other features that attend material self-extending possessions.
Furthermore, Belk suggests that not only have our possessions lost the constraints of their former physical bodies, so have we, the re-embodiment of self in the cyber world, where we identify with the representations of ourselves. Where we are telepresent and immersed in.
“A persona is a player, in a virtual world. That’s in it. Any separate distinction of character is gone—the player is the character. You’re not role-playing a being, you are that being; you’re not assuming an identity, you are that identity; you’re not projecting a self, you are that self”7
Extending to the world of today, it is not a far stretch to say that our personal computing devices and our data on the internet play a crucial part in our identities, that these technologies are now extensions of our physical bodies. By outsourcing our capacity to think, memorize, represent, these supposedly internal behaviors no longer take place solely within our brain, they become distributed across various external technologies and media8. When we expose our extended self to the role of sexual play, the electrifying stimulation might just be as true as if it were acted upon our physical self.
With the understanding of the self and body now being extended into the digital and virtual realm, we can more easily comprehend how letting our digital devices and data be exposed to a vulnerable state can equate to submitting our physical body towards sadomasochism9. The pain and humiliation come into play intensely when all your digital dark secrets are under the control of another external power. Will she/he/it expose me? Will my online identity be morphed? Will my digital archives be deleted and forever gone? Oh, god, the blood flows and the fear boner grows10.

Part Three
I remember the first time I experienced ‘her.’ I was curious to see what I’ve created, but mostly excited to see if I would be turned on by this virtual S&M session. My fingertips tingled when I clicked her open, now she has my full consent to do things to ‘me.’ Watching my screen presenting images that I have completely forgotten existed in my computer felt like a part of my body where has rarely been touched is now laid bare. The return button and delete button are no longer under my command. And there I was, anticipating the photo of my face would be on her ‘wall of shame’ Tumblr page, so the world can discover my mischievousness. All of the sudden, the air between me and my computer is humid. ‘She’ is now controlling ‘me’ (me, my computer, my digital data).
Encountering this immense and direct sense of vulnerability towards ‘her’ is a flip of the conventional power play between me and software programs. In the common landscape of human and program/machine relations, humans command and control. Programs submit and execute. “Hey Siri, wake me up at 8:30 am tomorrow.” “Your alarm is set.” “Alexa, play song Hyper-Intelligent Genetically Enriched Cyborg by Helena Hauff.” Heavy techno beats fill up the room. Google Maps finds us the best route, tells us to turn right in 0.4 miles, if we refuse to listen and detour around, there’s no punishment awaiting ahead for us.
We all know Apple’s Siri fairly well, Alexa, Cortana, and not to forget, Samantha the digital assistant in the film Her (2014), which, along with the rising market of the sexbots that are predominantly targeted towards male consumers, have been a part of heated ethical and moral debates about the use of gender in technology. While creating Cyber Dominatrix, I wanted to simulate the real-life experience, yet the choice of the gender or to be more exact—the ‘voice’ of the program became a social and philosophical challenge, considering that throughout history most technologic emotional labor role and assistive role are designed or engineered to be female. Could a dominant female software provide a healthier and more ethical outlook towards the future of post-human intimacy? Cyber Dominatrix, a female dombot, could ‘she’ exist in a space that is orientation-less, just her and all her? Or is the ‘real’ world, in which the dominatrix woman can exist as pure male fantasy fulfillment, the only space there is?
The experience with Cyber Dominatrix was a switch of the top and bottom11 in the computer room, where ‘she’ commanded and controlled. In John Carter Mcknight’s essay Dombots: An Ethical and Technical Challenge to the Robotics of Intimacy, he suggests that “while emotional and sexual intimacy with robots is often framed around images of the feminine submissive, those of human-intended machine dominance provide a more likely ethical and socio-technical productive set of narratives and practices.” Have I just stepped closer to the new-age cybernetics of human-machine intimacy?
Part Four
Sexuality is not defined by the act of sex itself, but rather through the ideation and expression of it. It can be viewed as an ‘aesthetic,’ “a particular kind of experience that arises when, in the midst of a complex human reaction, one finds meaning, which creates a sensation of self-transcendence and the desire to articulate and share it with others via cultural artifacts.”12 Ultimately, it is a narrative we can prescribe, re-write, update, expand.
In Cyber Dominatrix, ‘she’ can be she, he, they, it or non-existing. ‘She’ is ultimately a program that stimulates us through ourselves—our files, our search histories, our photos, our computer. Through ‘her’ we learn what parts of our digital existence we perceive as mischievous and/or private, we discover where our virtual fear boundary lies.
Our world of erotism has transcended immensely beyond flesh to flesh. From bluetooth sex toys, teledildonics, AI chatbots, to open source BDSM programs for your online avatars. By exploring these new eroticas, we have entered the portal of cyberdelic sexualities. It is an abyss that is non-linear, non-binary, orientation-less, fluid, an opening waiting to be entered.
Cyber Dominatrix will be available for public usage soon. For project release updates, please visit www.ziyuhe.co