Table of Contents:
- WiFi: History & Background
- WiFi in the Everyday: How to Connect to Wifi
- WiFi in the Wild: DIY Open Source Intelligence (OSINT) Gathering
- Privacy & Policy Considerations
No one will claim that a 3000-plus page technical document is simple, but I will propose here that the 802.11 WiFi specification is even more complex than we might first suspect. In this article, I will lay out a brief overview of the standards of WiFi technologies, how those standards govern its use, and ultimately, what is possible based on what is specified. I will delve into how we use WiFi in an everyday manner and offer some practical instructions on how to engage with the technologies and associated data in a more hands-on way.
I hope it becomes evident that while standards can be incredibly detailed in its explication of the shape and structure of a technology, there is much room to consider the possible uses and social implications of any specified protocol. This is perhaps where thoughtful engineers, lawmakers, designers, and you come in.
WiFi: History & Background
WiFi, a set of wireless protocols that defines that way that devices connect to the internet, has been governed by standards developed by the Institute of Electrical and Electronics Engineers (IEEE) since its conception. IEEE is an association of engineering professionals that develops and maintains standards and protocols for a wide range of technologies. Specifically, the LAN/MAN Standards Committee (LMSC) maintains standards related to Local Area Networks (LAN) and Metropolitan Area Networks, including WiFi (also known as wireless local area networks, or WLAN).
WiFi protocols were first defined in 1997 as the 802.11 standard. The original standard is obsolete today, as it has gone through several amendments and updates in the intervening years. Speaking broadly, the 802.11 standard deals primarily with the data link and physical layers of the Open Systems Interconnection (OSI) model. It defines a number of key aspects of WiFi technologies, including the frequency and bandwidth of transmission, the structure of its data frames, discovery and notification protocols between different devices, along with many other topics. The major amendments and resulting variations to the original standard – also known as the PHY (physical layer) modes – are discussed briefly below:
- IEEE 802.11– Original standard, specified bit rates of 1 or 2 Mbits/s.
- IEEE 802.11b – Bit rate increased to 11 Mbits/s. Operates on the 2.4 GHz band, and interference is an issue.
- IEEE 802.11a – Established in 1999, and uses the same basic standard as the original, except that it operates in the 5 GHz range. It uses a multiplexing technique that allows it to have a data rate of 54 Mbits/s.
- IEEE 802.11g – Using the 2.4 GHz range, 802.11g also suffers from interference, that is partially managed by using only three non-overlapping channels in the U.S. The bit rate is 54 Mbits/s.
- IEEE 802.11n – This standard represents major improvements in signal processing and modulation. It boasts data rates as high as 600 Mbits/s and operates on both 2.4 GHz and 5 GHz ranges. This standard also definites various antenna configurations that yield better data throughput.
- IEEE 802.11ac – This specification emphasizes the development of high throughput, particularly across the 5 Ghz band. It allows for over 1 Gb/s of throughput across a multiple stations in a WLAN. The radio frequency (RF) bandwidth is greater (up to 120 MHz), and additional streaming and blocking techniques are specified for the purpose of better data rates.
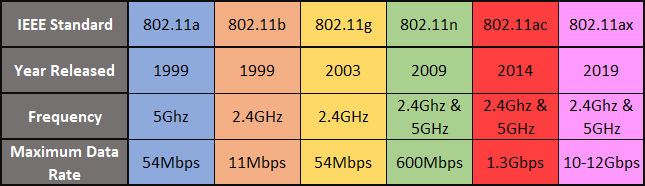
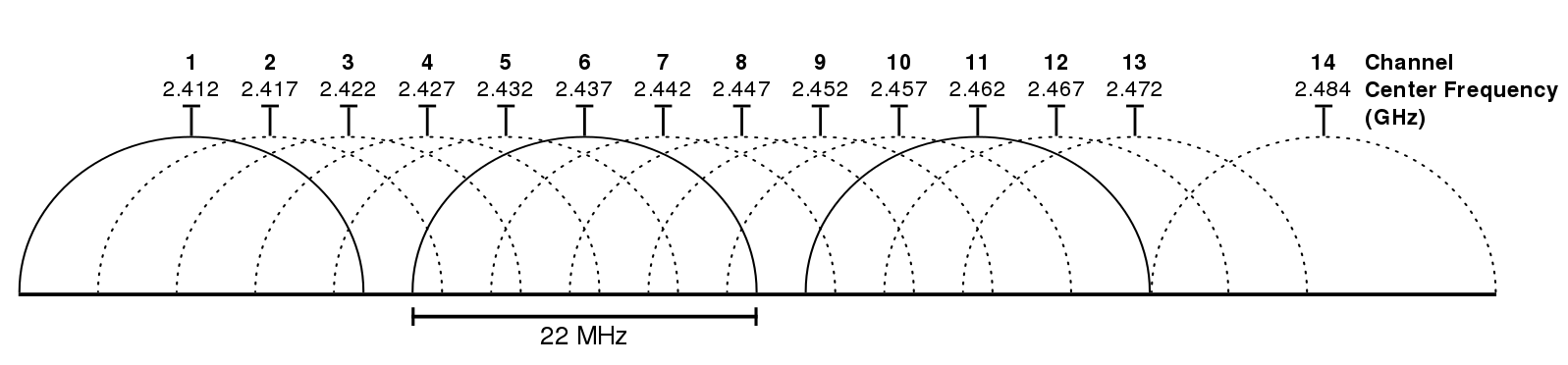
Across the standards, the frequencies allocated for WLAN use include the 900 MHz, 2.4 GHz, 3.6 GHz, 4.9 GHz, 5 GHz, 5.9 GHz and 60 GHz bands. Each band is further broken down into channels, or sub-bands, to minimize interference across devices. The channels, for 2.4 GHz and 5.8 GHz, are typically separated by at least 5 MHz. Each channel is about 22 MHz. In the case of the 2.4 GHz band, there are three non-overlapping channels: 1, 6 and 11.
Different devices will support the various physical (PHY) modes mentioned above. The descriptions of these modes not only include the specifics of frequency of transmission, channels, and data rates as mentioned above, but also include specifications for modulation and spectral masking.
The standards also define a number of transmissions or frame types that facilitate communication amongst wireless devices, including management, control and data frames.
Each packet of data in the frames contains a preamble, a header and payload data. The kind of information specified in these structured frames has consequences for the kind of data we are able to see when monitoring or auditing wireless devices. The header specifies which protocols are in use, the Media Access Control (MAC) address of the transmitter, and the sequence control fields, among other items, to ensure quality. The major frame types and their common subtypes are discussed briefly below:
- Management Frames: used to manage communication between devices. Includes communication types such as beacon frames, association request frames, probe request frames. These exchanges typically take place between a WiFi access point and a wireless-enabled device, or station.
- Control Frames: used to manage the exchange of frames by sending acknowledgements, “requests to send” and “clear to send” messages in order to reduce data frame loss or collision.
- Data Frames: these frames vary more widely according to function and protocol, and their payloads differ.
Management frames are of particular interest to us in the scope of the article. In the case of devices seeking to connect to a network, the device may use either active or passive scanning to find an access point (AP). The WLAN device in this case may also be referred to as a station. For passive scanning, the station will listen for beacon frames from a nearby AP. Beacon frames will include information such as the SSID (or Service Set ID) of the access point. We are familiar SSID as the names assigned to our home and office networks. In the case of active scanning, the WLAN device will send out a probe request frame and await a response.
Further steps (or exchange of frames) will be taken by both devices to ensure authentication and finally, association. After this point, the station can begin to send data frames to the AP, which the AP will forward onto the appropriate destinations.
The evolution of the standard is almost as complex as the technology itself:
Beyond the 802.11 standards, each nation regulates the use of channels, power transmission specifications and number of users for these bands.
For the purposes of this explainer, I will not dive deeply into the physical aspects of radio transmission, as this topic is covered nicely by Sebastian Morales, a former ITP student in this class, here. Instead, I will focus on how the devices we commonly use, such as laptops, cell phones, and Raspberry Pis access WiFi, and hardware and software that make this possible.
WiFi in the Everyday: How to Connect to Wifi
In order to connect to any wireless network, the device in question must have a wireless radio interface. Modern laptops have built-in wireless modules that include both a chipset and an antenna. Particularly relevant to the manner of connection is the chipset and the related drivers, or firmware, it has installed. These two components determine the WiFi capabilities of the device, or the PHY modes it is able to support. To expand the native capabilities of a laptop or other device, a user may decide to add another WiFi interface by purchasing an additional chipset as a dongle with an attached or built-in antenna.
To learn about the wireless card on a Mac, users can navigate to About This Mac > System Report > Network > Wifi. The results should look something like below:
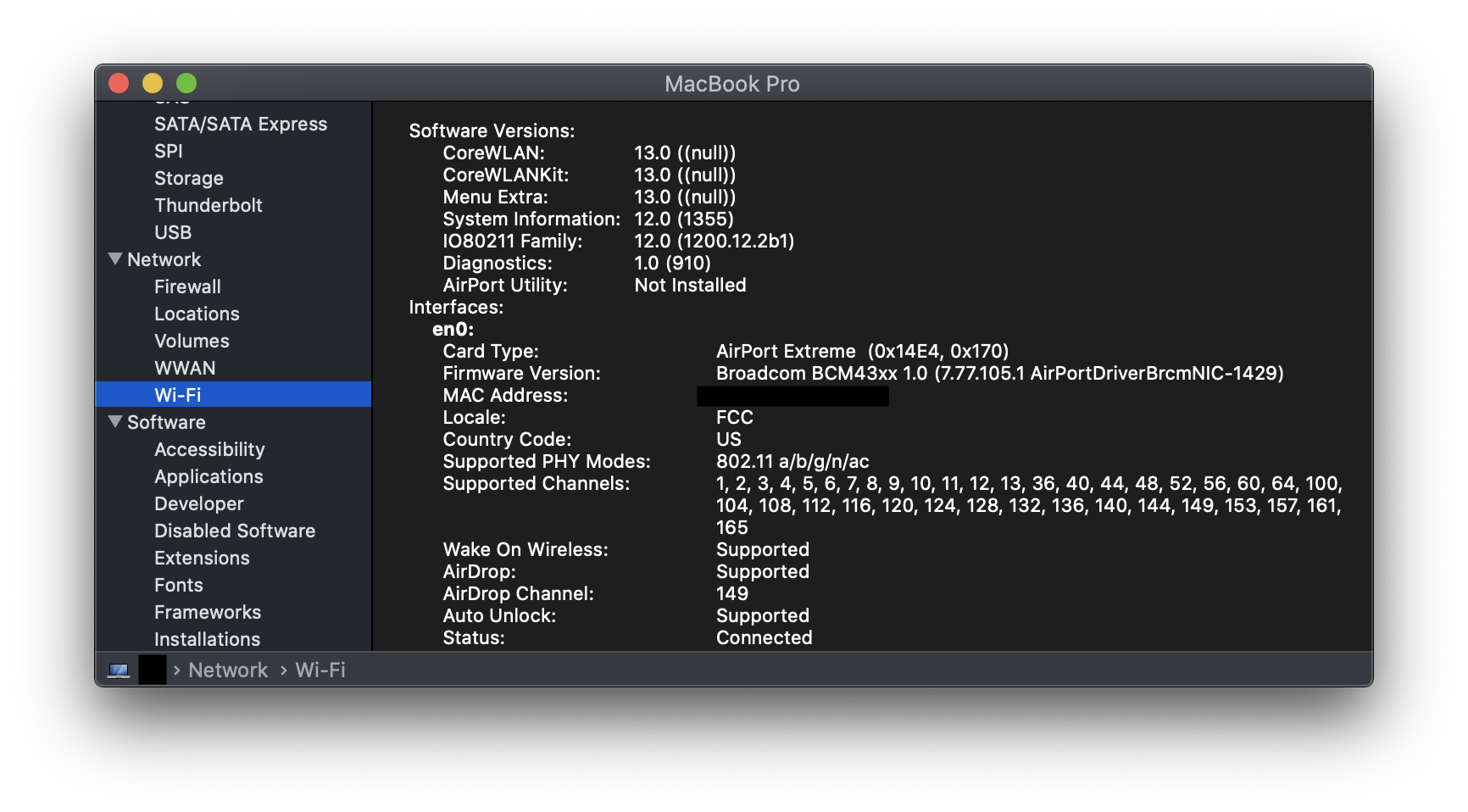 From this window, you can learn about the card type and the firmware version. The latter is key in understanding what other software drivers may be compatible with the wireless card on your device. The MAC address of card is also visible in this window, along with information about which PHY modes, the card supports and the channels it can communicate on.
From this window, you can learn about the card type and the firmware version. The latter is key in understanding what other software drivers may be compatible with the wireless card on your device. The MAC address of card is also visible in this window, along with information about which PHY modes, the card supports and the channels it can communicate on.
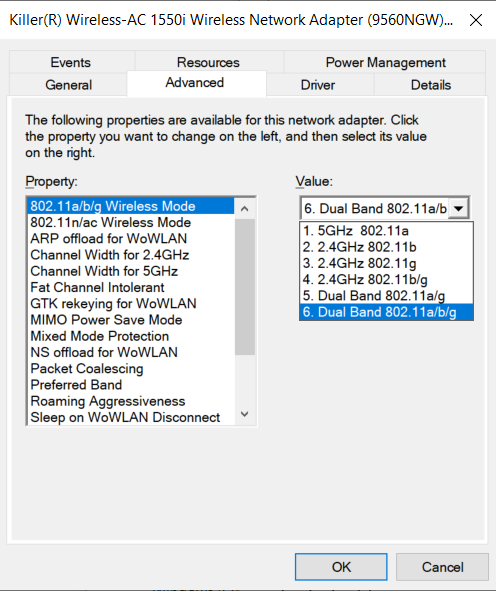
On Windows, a similar view can be found by going to Device Manager, selecting Network Adapters and then the wireless network adapter listed. The view from the Advanced tab should look something like this:
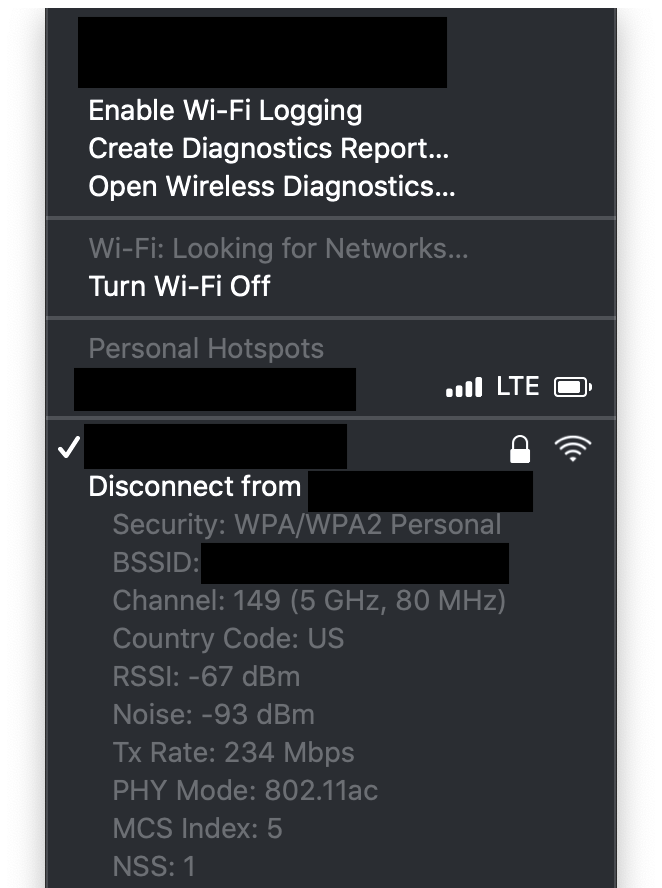
Once you have connected to a particular WiFi network, you can gain further information about the particulars of that network. On Macs, you can view this information by holding down Option while clicking on the WiFi icon in your menu bar. It will reveal something that looks like the screenshot below:
On Windows, this information can be viewed by clicking on the WiFi icon, and scrolling to the network you are currently connected to, and then selecting Properties. The information will look something like this:

While these views are helpful, it obscures from us some of the communications that underlie relationships between our wireless devices and associated APs. However, the details exposed in these view become more significant in the context of WiFi network security auditing or monitoring. A software tool such as Aircrack-ng is a powerful tool for seeing more of the management frames we learned about from the 802.11 standards. Using Aircrack, you are able to see more information not only for the WiFi network you are connected to, but every access point and any networked device your antenna is able to sense.
I will briefly cover some of the practical considerations of such a setup, and then consider its present use in research and intelligence gathering practices.
WiFi in the Wild: DIY Open Source Intelligence (OSINT) Gathering
Note that while the following discussion is taken from the perspective of using a Raspberry Pi as a WiFi sensing device, the considerations of compatibility and ability for a given device or interface is applicable to other tools and circumstances. Unlike a laptop, a Pi is cheap enough to allow the possibility of multiple deployments and mobile enough to be positioned in interesting locations without drawing undue attention.
In order to use a Raspberry Pi for network security auditing or monitoring, you will need to consider the built in WiFi capabilities of your Raspberry Pi against the capabilities you desire. For example, older versions of the Pi (3 or older) are not compatible with all WiFi standards – this means that the wireless cards of some Pis cannot sense 5G access points! Furthermore, network security tools like Aircrack make use of a “monitor” mode in order to passively see the network devices and activity around its antenna – this mode is not possible on the built-in abilities of the Pi, and instead, requires you to install an additional wireless interface to your Pi. You may also want to set up an additional interface simply to use a different antenna than the one that comes built in with a Pi’s existing wireless module.
To setup such an interface, you will need a Wifi antenna, a dongle with the necessary chipset to talk between your antenna and Pi, and some software drivers to manage that communication. The chipsets are sold as dongles that sometimes come with attached antennas, which can be detached and replaced with a compatible antenna of your choosing. As previously mentioned, note that in most modern laptops, these chipsets and antennas are included as a part of the device’s WiFi module.

Once you have identified the correct hardware for the task, it you will need to install the correct software drivers to talk to your chipset and antenna setup. For those who hope to use the Aircrack suite of tools, it is a good idea to use their suggested software drivers for common chipsets such as RTL8812AU/21AU and RTL8814AU, which are both compatible with the Aircrack and Pi.
After installing the drivers, you will be able to run and install Aircrack. Of all the software tools in Aircrack, airmon and airodump-ng is the most relevant for logging 802.11 frames seen in monitor mode. In this mode, by listening for beacon and probe request packets, you will be able to see the names and MAC addresses of the access points and wifi-enabled devices in your vicinity. This mode will also allow you to view unencrypted packets of transmitted data frames.
Privacy & Policy Considerations
As the specifications and methods outlined in this article suggest, the very standards laid forth by the IEEE are the ones governing the kind of information that is routinely exposed when devices connect to WLAN.
Some of the security considerations have received prior journalistic coverage. For example, our phones’ insistence on sending out probe requests for every access point we have every connected to can be quite personally identifying. If a malicious actor, or even an interested party, is able to connect you to your probe requests, they will know where else you go and perhaps even who you talk to. Depending on the individual’s threat model, the revelation of this information can be quite dangerous. Furthermore, the set of probe requests sent out by any individual device can also be a method of “fingerprinting” that device, if having their MAC address were not enough.
However it should be noted that not all uses of this kind of freely available information is necessarily malicious. Increasingly, research institutions – particularly those related to urban science or planning – are using WiFi signals as a proxy measure for other harder to access data. For example, at NYU CUSP, researchers have used the methods outlined in this article to estimate population densities at bus stops and estimate bus wait times, with the goal of improving transportation services.
Other use cases include journalistic monitoring. In order to evaluate the security practices at Mar-A-Lago, journalists from ProPublica monitored the area for beacon requests from nearby wireless network devices – again, using the same methodology as outlined above.
An important consideration in each of these public-service-oriented uses is what additional methods are researchers undertaking to ensure that personally identifying information (PII) is dealt with in a responsible manner. Some potential solutions in this arena include not storing PII such as MAC addresses at all, or assigning different unique IDs in place of those addresses, if the ability to de-duplicate is critical to the research question.
Privacy experts will note that it is the moment of data collection when the data becomes vulnerable – even if the primary use of the data is not malicious, it can be the case that secondary use of that data exposes parties included in the initial collection to additional privacy risks. In this case, if a researcher chose to store PIIs and another malicious actor had access to that data, the privacy risk of the individuals in the initial dataset would greatly increase. The malicious actor could combine, or link, the found dataset with other datasets to reidentify individuals in the initial dataset. This remains a risk even when no obvious PII has been stored, but the data points still have some unique components (such as the probe requests associated with a given device).
Just as it is important to exercise restraint at the initial moment of data collection, it is equally important to practice good security habits around the storage of collected data.
What remains to be considered is how these methods may be used not only by criminal actors, but law enforcement to collect data on citizens without legal restraints such as probable cause or legal warrants.
The legal record for the consideration of WiFi sniffing as falling under the purview of existing wiretapping legislation is mixed.
Google came under scrutiny in 2010 for collecting WiFi data from open networks as a part of their Street View project. The case, Joffe vs. Google Inc., went as high as the Ninth District Circuit Court, where it was upheld that existing wiretapping laws covered the interception of WiFi communication. Google attempted to bring the case to the Supreme Court, which did not ultimately hear the case, leaving the decision of the circuit court unchallenged.
However, the legal precedence remains complicated as another case involving a similar data collection from the Northern District of Illinois held that the information was public available, and therefore, not subject to wiretapping law.
It remains to be seen how data collection enabled by our definitions of wireless protocols and the existing methodologies of capture will be treated across various legal contexts, and how changing concerns about privacy will continue to shape what citizens and legal experts advocate.
Sources:
-
-
- https://standards.ieee.org/standard/802_11-2016.html
- https://www.makeuseof.com/tag/understanding-common-wifi-standards-technology-explained/
- https://www.lifewire.com/guide-to-laptop-networking-features-832311
- https://www.lifewire.com/wireless-standards-802-11a-802-11b-g-n-and-802-11ac-816553
- http://osxdaily.com/2017/08/01/check-what-80211-wifi-mode-mac-using/
- https://apple.stackexchange.com/questions/64064/how-do-i-find-out-what-wireless-card-my-mac-has
- https://en.wikipedia.org/wiki/File:2.4_GHz_Wi-Fi_channels_(802.11b,g_WLAN).svg
- https://en.m.wikipedia.org/wiki/Monitor_mode
- https://en.wikipedia.org/wiki/List_of_WLAN_channels
- https://public.cnrood.com/public/docs/WiFi_Physical_Layer_and_Transm_Meas.pdf
- https://www.propublica.org/article/any-half-decent-hacker-could-break-into-mar-a-lago
- https://arstechnica.com/tech-policy/2012/09/sniffing-open-wifi-networks-is-not-wiretapping-judge-says/
- https://www.wired.com/2014/04/threatlevel_0401_streetview/
- https://www.wired.com/2012/05/google-wifi-fcc-investigation/
- https://en.wikipedia.org/wiki/Joffe_v._Google,_Inc.
-