For a more detailed explanation of many of these terms, see the Explanations Page.
A
AES
AES is short for Advanced Encryption Standard, and it is a symmetric 128-bits (or 16 bytes) block cipher (A block cipher is a method of encrypting data in blocks to produce ciphertext using a cryptographic key and algorithm) that is widely used to encrypt the transfer of data online. It appeared commonly in VPNs, Wi-Fis, mobile applications and even programming language libraries. It takes 128-bits of a message, a file or any data that needed to be encrypted, and encrypts them into 128-bits cipher text with a key that can either be 128-bits, 192-bits or 256 bits. And more bits they key is, the more secure the data is.
First, AES arranges the data (plain text that is not written in code) into the a 4×4 block of bytes, and then it relies on substitution-permutation network principle to operate the data with process of key expansion, adding round key, byte substitution, shifting rows, mixing columns, rinse and repeat to generate ciphertext. Although AES requires less memory and processes encryption and decryption faster, the fact that it uses single key to encrypt and decrypt the data can create a potential gateway for hackers to intercept the key.
See also Cryptography
References:
- https://cybernews.com/resources/what-is-aes-encryption/
- https://www.geeksforgeeks.org/advanced-encryption-standard-aes/
- https://www.youtube.com/watch?v=O4xNJsjtN6E&t=163s
– Erin Tao
ARP
The Address Resolution Protocol is the communication protocol used to link layers 2 and 3 of the OSI model. Layer 2 is the data link layer and can be associated with the MAC address of the device. ARP links the MAC address to layer 3 of the OSI model, the network layer, typically an IPv4 address.
ASCII
ASCII stands for American Standard Code for Information Interchange. It is a character encoding standard for electronic communication. This standard is used to represent text in computers, telecommunications equipment and other connected devices.
Originally based on the English alphabet, ASCII encodes 128 specified characters into seven-bit integers.
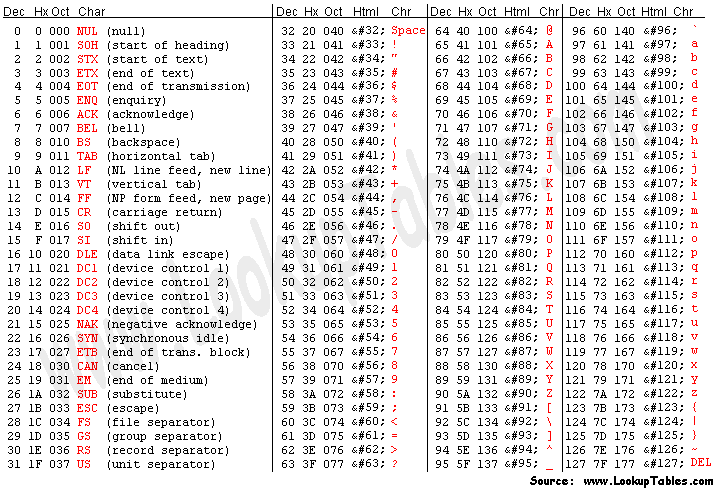
This table is used behind the scenes of our everyday communication when we interact with our devices, such as computers. Our devices translate “computer text” to “human text” so that we can read it. Computers speak in terms of 1’s and 0’s, aka binary, and they use their own language, ASCII, in order to communicate as well as translate messages so that we can understand them.
ASCII was was incorporated into Unicode in 1991 since Unicode and the UCS support more characters by separating the concepts of unique identification (using natural numbers called code points) and encoding (to 8-, 16- or 32-bit binary formats, called UTF-8, UTF-16 and UTF-32). ASCII characters have the same numeric codes in both sets which allows UTF-8 to be backwards-compatible with 7-bit ASCII. Forward compatibility is also ensured because software that recognizes only 7-bit ASCII characters as special and does not alter bytes with the highest bit set will not change UTF-8 data.
References:
– Ben Moll
Asymmetric Encryption
Asymmetric Encryption -Uses a pair of related keys (a private key and a public key) to encrypt and decrypt messages. The public key is visible by everyone and can be used by anyone who wants to send a message. The private key is only known by the creator. When someone would like to send you a message they will use your public key to encrypt the message. Only your private key can decrypt the message.
When you encrypt a message with your private key, anyone with your public key can decrypt the message, but the fact that a message has been decrypted with your public key means it must have been encrypted with your private key. Therefore the only person who could have created the message is you because you are the only one with the private key. This serves as proof that the message is “digitally signed” by you.
The most secure way to send an encrypted message would be to encrypt the message using your private key and the receiver’s public key. This way only the receiver can decrypt it and it will be “digitally signed” by you, ensuring that you were the person who sent the message.
Asymmetric encryption uses complex “trapdoor” one-way mathematical functions and very large random numbers to create the public and private keys.
One-way function is a function that is easy to compute in one direction but difficult to reverse, unless you have special information.
The most commonly used asymmetric encryption algorithm used today is called RSA encryption.
See also Cryptography
– Gracy Welihan
Authentication
A cybersecurity process that confirms that a user or user device is ‘who they say they are,’ most often used in the context of the user or device asking for access to resources over a network. Typically paired with an Authorization process. See this explainer for more.
Authorization
A cybersecurity process that confirms a user or user device is allowed to access the resource they are trying to reach. Typically paired with an Authentication process. See this explainer for more.
– Christina Tang
B
Bit
A bit (binary digit) is the smallest unit for computational processing. It can be either on/off, also known as 0 or 1.
References:
https://www.techtarget.com/whatis/definition/bit-binary-digit
– I-Jon Hsieh
Bitrate
Bitrate describes the rate at which bits are transferred from one location to another. It measures how much data is transmitted in a given amount of time. Bitrate is commonly measured in bits per second (bps), kilobits per second (Kbps), or megabits per second (Mbps).
– Sihan Zhang
Bogon
A bogon is an informal term used to describe an illegitimate IP address. Some IP packets on public internet claim to be coming from an IP address that is in use, but has not yet been delegated by the Internet Assigned Numbers Authority (IANA)*. These IP address can’t be associated to an actual host, which makes them bogus and unable to be geolocated.
You may see these addresses pass through your router, as it does not care about a source IP address (the bogon) but only the destination IP address. These bogons aren’t static either, but are dynamic and the addresses get changed over time.
References:
- Bogon IP Address Ranges
- Bogons: Do Not Let Them In Or Through Your Networks
- IANA Functions: The Basics
– Bianca Gan
Buffer
A Buffer, also known as data buffer, refers to a region of memory that temporarily holds data right before it is used. In telecommunications, buffers help to compensate for momentary delays, such as rate differences while data transferring from one device to another.
References:
– I-Jon Hsieh
Byte
A byte is a common unit of data. One byte consists of 8 bits (1 byte = 8 bits). It is used to store numbers. A single byte can represent 256 (28) numbers. It can also represent characters, such as letters or symbols, by converting numbers to ASCII code.
References:
- https://www.britannica.com/technology/byte
- https://www.intel.com/content/dam/www/program/education/us/en/documents/the-journery-inside/digital/tji-digital-info-handout4.pdf
– I-Jon Hsieh
C
Cache
A cache temporarily stores data for future requests. This enables the data to be retrieved faster and improves performance. Cache is commonly used by web browsers, as well as CPU, applications, and operating systems. When a client (ex. Chrome) tries to access data, it will first check whether the data is stored in the cache. If not, it then needs to get the data from the main memory (web server), at the same time, the data will be stored in the cache.
References:
https://www.techtarget.com/searchstorage/definition/cache
– I-Jon Hsieh
Certificate Authority
Certificate Authority – Trusted organization that validates content on the internet by authenticating public keys. See also Cryptography
– Gracy Welihan
Ciphertext
A Ciphertext is the result of an encrypted message.
See also Cryptography
– Gracy Welihan
Cryptography
Cryptography is a method for protecting communication and information through codes. The codes ensure that only the intended person receives, reads and processes the message. Cryptography is essential for:
- Confidentiality
- Integrity
- Non-repudiation
- Authentication
See also:
- Ciphertext
- Private Key
- Public Key
- Key pair
- Symmetric Encryption
- Asymmetric Encryption
- Digital Signature
- End-to-end Encryption
- Certificate Authority
- AES
- RSA
References:
- Public Key Cryptography – Computerphile
- Explaining public-key cryptography to non-geeks
- Gambling with Secrets: 8/8 (RSA Encryption)
- asymmetric cryptography (public key cryptography)
- What is Asymmetric Encryption? Understand with Simple Examples
– Gracy Welihan
CSS
CSS stands for Cascading Style Sheets. CSS dictates how the HTML elements of a website should appear in a browser. CSS communicates defines the styles of objects in the HTML DOM, and its definitions are applied to HTML elements on page load to finish the look of elements. They are like the paint, color, and facial expression printed on LEGO persons, further articulating their visual characteristics .
References:
– Rockey Ke
Checksum
A checksum is a small-sized block of data derived from a larger block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. Checksums are often used to verify data integrity but are not relied upon to verify data authenticity. A good checksum algorithm outputs a significantly different value for even the smallest change made to the input (e.g. the change of one bit). If the computed checksum for the current data input matches a stored value of a previously computed checksum, there is a very high probability that the data has not been accidentally altered or corrupted.
An inconsistent checksum number can be caused by an interruption in the network connection, storage or space issues, a corrupted disk or file, or a third party interfering with data transfer.
Programmers can use cryptographic hash functions like SHA-0, SHA-1, SHA-2, and MD5 to generate checksum values. Common protocols used to determine checksum numbers are TCP and UDP. As an example, the UDP checksum algorithm works like this:
- Divides the data into 16-bit chunks
- Add the chunks together
- Any carry that is generated is added back to the sum
- Perform the 1’s complement of the sum
- Put that value in the checksum field of the UDP segment
References:
- https://en.wikipedia.org/wiki/Checksum
- https://www.techtarget.com/searchsecurity/definition/checksum
- https://www.educative.io/answers/how-does-checksum-work
– Priyanka Makin
CDN
The acronym CDN stands for Content Distribution Network. A CDN is a network of proxy servers and data centers placed around the globe. Their purpose is to enable speed and efficiency of content delivery to end users. A CDN does not host content; instead its purpose is to cache content with the goal of improving website performance, prevent site interruptions, strengthen site security and reduce hosting costs.
CDNs improve website speed by reducing the distance travelled between a user and website’s resources. They allow a user to connect to the geographically closest data center, facilitating a reduction in travel time for the data and therefore allowing for faster load times. In order to optimize the response quality, the location best for serving content to a user might be calculated based on the fewest number of hops, lowest number of seconds for the data to travel, or most available server.

CDNs also balance traffic (”load balancing”), distributing data requests during spikes in traffic. This allows CDNs to play a significant mitigating the potency of in DDoS (Distributed Denial of Service) attacks and improving the security of websites.
A CDN also reduces the amount of data transferred between the user and the origin server (”bandwidth”) through reductions in file sizes (through minification or file compression). Similarly, CDNs cache the content of websites so that less data needs to travel in and out of the web host’s server, therefore lowering bandwidth costs.
References
– Martha Janicki
CORS
Cross-Origin Resource Sharing. See this explanation.
D
Datagram
A datagram is a basic transfer unit associated with a packet-switched network. Each datagram has two components, a header and a data payload. The header contains the information sufficient for the packet to be delivered from its source to destination. The payload is the actual data to be transported.
Reference: Wikipedia
– Tuan Huang
DHCP
Dynamic Host Configuration Protocol ( DHCP ) is a protocol that allows the router to dynamically assign computers connected to the network an IP address from the pool of ones available network. The DHCP server keeps track of which IP address have been assigned to which devices. In this way, if you disconnect from the network, and rejoin it, your device will keep the same IP address.
Digital Signature
Digital Signature – An encrypted message is digitally signed when an individual’s private key is verified by the public key. Digital signatures offer:
- Authentication – since the unique private key was used to apply the signature other can be sure that the person with the private key was the one who actually applied the signature
- Non-repudiation – the individual with the private key cannot later claim that it wasn’t them who applied the signature
- Integrity – when the signature is verified it checks that the information in the message matches what was there when the signature was applied.
- Confidentiality – the content encrypted with a public key can only be decrypted with the matching private key. Ensuring only the individual with the private key can decrypt the message.
See also Cryptography
– Gracy Welihan
DOM
DOM, or the Document Object Model, is a system of organizing and structuring web file content that allow other programing languages to access and manipulate them. For this purpose, it has been adopted as a standard in making web files more modular. The O(object) in DOM signify its main characteristic, which is to organize web pages into series of “objects”. These are the object building blocks for web content. Starting from more primitive ones in the core DOM, such as Document, Node, Element, Nodelist etc, DOM can be expanded and include more detailed elements such as headers, images etc. The DOM commonly integrates JavaScript, HTML, and Cascading Style Sheets (CSS), though it can also be used to connect Javascript of other programming languages to other markup languages like XML. Consider the objects as LEGO parts, and the parts in core DOM are the smallest pieces of LEGO bricks that you cannot split further.
References:
– Rockey Ke
DNS vs MDNS
DNS vs MDNS – DNS protocol is Domain Name System protocol. Used to assign human readable domain names to IP address for easy navigation across the web. For more on DNS, see this explanation. Similarly MDNS (multicast DNS, see below) is a local net protocol used for name resolution of a smaller, usually local network. Local networks do not need to query a name server and all local devices have a direct address
– Jake Sherwood
E
Encapsulation
In a networking context, the method of nesting the data payload in a packet with a header is known as ‘encapsulation’.
End-to-end Encryption
End-to-end Encryption – For two devices to communicate with each other they need an intermediate server. With end-to-end encryption the server will not encrypt or decrypt the messages, they will only pass the encrypted messages along. Each user will encrypt and decrypt the messages on their devices using public and private keys.
See also Cryptography
– Gracy Welihan
Ethernet Frame
An Ethernet Frame is a message used in the data link layer. See Jingyuan’s definition of Packet vs. Frame.
– Bianca Gan
Evil bit
An Evil bit is a fictional IPv4 packet header field proposed to a Request for Comments (RFC) publication for April Fool’s in 2003. The RFC recommended that the last unused bit, the “Reserved bit” in the IPv4 packet header be used to indicate whether a packet had been sent with malicious intent, thus simplifying internet security.
The RFC states that benign packets will have this bit set to 0; those that are used for an attack will have the bit set to 1. Firewalls must drop all inbound packets that have the evil bit set and packets with the evil bit off must not be dropped. The RFC also suggests how to set the evil bit in different scenarios:
Attack applications may use a suitable API to request that the bit be set.
Packet header fragments that are dangerous must have the evil bit set.
If a packet with the evil bit set is fragmented by a router and the fragments themselves are not dangerous, the evil bit can be cleared in the fragments but reset in the reassembled packet.
Applications that hand-craft their own packets that are part of an attack must set the evil bit.
Hosts inside the firewall must not set the evil bit on any packets. (RFC 3514)
Reference:
- RFC Editor, RFC 3514
- https://en.wikipedia.org/wiki/Evil_bit
– Priyanka Makin
F
Firewall
What is a firewall? A firewall is a network security device that controls and monitors incoming and outing network traffic based on a series of security rules that have been predetermined. It can be hardware, software, software-as-a service, public cloud, or private cloud. It filters and blocks unauthorized traffic to prevent attacks. The first published paper on firewall technology was in 1987 by engineers from Digital Equipment Corporation. It was called as a packet filter firewall at that time.
What is a hardware firewall?It has basically the same functions as a software firewall but is deployed as a physical appliance. It can provide consistent security to all devices that it protects without varying configurations for each device. It can also improve security because it runs on its own dedicated hardware independently instead of relying on resources of the device where it is installed.
Example of a hardware firewall: Cisco Firepower 4100 Series – NGFW Appliances
How does a firewall work? Firewalls control the network traffic by allowing or denying requests at specific ports. The predetermined rules will specify which port number allows what kind of source addresses to go through.
How to set up a firewall on a linux device?
References
- https://www.forcepoint.com/cyber-edu/firewall
- https://itp.nyu.edu/networks/setting-up-a-firewall-on-an-embedded-linux-device/
- https://www.checkpoint.com/cyber-hub/network-security/what-is-firewall/what-is-a-hardware-firewall/
– Lily Yu
Front-End vs. Back-End
Front-end developers work on what end users on the web can see, while back-end developers build the infrastructure that supports it.
Front-end development focuses on the user-facing side of a website. Front-end developers design and construct the user experience elements on the web page or app including buttons, menus, pages, links, graphics and more.
The three primary front end languages in use are HTML, CSS, and Javascript. HTML provides the structure of the website, while CSS provides the visual look, and Javascript provides the interactivity. Any front-end programming code runs on the client’s machine (e.g. HTML, CSS, and JavaScript).
The back-end, also called the server-side, consists of the server which provides data on request, the application that channels it, and the database which organizes the information.
The most popular languages for the back-end are PHP, Ruby, Python, SQL, and Java. The purpose of these languages is to interact with the websites database. These languages are intended to store, retrieve, and change specific information stored in the data files. Any back-programming code runs on the server’s machine.
References:
- What Is the Difference Between Front-End and Back-End Development?
- The Difference Between Front-End vs. Back-End
- FRONT END VS BACK END OF YOUR WEBSITE: EVERYTHING YOU NEED TO KNOW
– Michelle Xu
FTP & SFTP
What is FTP? FTP stands for File Transfer Protocol. It is a network protocol for transmitting files between a client and a server. It makes transferring larger or multiple files more efficient. A client will be able to upload or download files after they successfully connect to the FTP server.
What is a network protocol? A network protocol is a set of rules to predetermine how to format, transmit, and receive data for devices in computer networks to communicate with each other.
What is SFTP? SFTP stands for Secure File Transfer Protocol or SSH File Transfer Protocol. It uses secure shell encryption (the SSH protocol) to provide security for file transmission.
What is SSH? The SSH protocol, also called as Secure Shell, provides strong authentication and encryption to increase security in network communications.
References
- Original sources:
- FTP: https://www.rfc-editor.org/pdfrfc/rfc114.txt.pdf (developed in 1971)
- SFTP: https://datatracker.ietf.org/doc/html/draft-ietf-secsh-filexfer-00 (developed in 2006)
- SSH: https://www.rfc-editor.org/pdfrfc/rfc4250.txt.pdf (developed in 2006)
- https://en.wikipedia.org/wiki/File_Transfer_Protocol
- https://www.techtarget.com/searchnetworking/definition/File-Transfer-Protocol-FTP
- https://www.precisely.com/glossary/sftp
- https://www.ssh.com/academy/ssh/protocol
– Lily Yu
G
Gateway
Broadly, a gateway is a computer that sits between different networks or applications. The gateway converts information, data or other communications from one protocol or format to another.
To be more specific, a Network Gateway is designed to translate traffic and transmission protocols between different networks. This is called Network Address translation (NAT). The two key features of a network gateway are multi-protocol support and visibility. They are typically designed to support multiple protocols, making it easier to setup interfaces between different networks. And since gateways are deployed at networks boundaries, giving them unmatched visibility into the traffic crossing these boundaries allows us to differentiate a public Internet and private internal networks.
Reference:
– Tuan Huang
gif
A gif is an image format, using the Lempel-Ziv-Welch (LZW) lossless compression technique to reduce file size without degrading the visual quality. It uses up to 8 bits per pixel and maximum of 256 colors from the 24-bit color space and allows a separate palette of 256 colors for each frame. Gifs are often used for animations or emotional reactions on social media.
Disagreement over the pronunciation of the word. Steven Wilhite, the creator of the format, told the New York Times in 2013 that the word should be pronounced using a soft g like in Jif the peanut butter brand. However, polling has found that pronouncing the word with a hard g is more prevalent.
References
– Martha Janicki
H
Host
A host is simply a computer system attached to the internet. It could be a single physical device running its own operating system, or it could be a virtual instance of an operating system, hosted along with many other instances on a computer elsewhere in the world. All hosts on the internet have IP addresses, either public or private.
HSRP
HSRP – Hot Standby Redundancy Protocol, as the name states is a redundancy protocol. Developed by CISCO it creates a series of virtual routers all sharing a single MAC address and IP. The “active” router is the gateway to the local network and should it fail a “standby” router will become active and begin to forward traffic.
– Jake Sherwood
Hypertext Transfer Protocol (HTTP)
Hypertext Transfer Protocol (HTTP) is a request-response application-level protocol based on the client-server model. HTTP is a TCP/IP based communication protocol that’s used to deliver data (HMTL files, images, query results etc.) between computers in a standardized way. Basically, it’s responsible for transporting most of the data across the world wide web. The connection defaults to TCP port 80. HTTP is both connectionless and stateless. This means that once an HTTP request is made, the client disconnects from the server and waits for a response. When the server responds, it re-establishes the connection in order to send the response. The fact that HTTP is stateless refers to the fact that the clients are only aware of each other during the current request. Once it’s over, they forget about each other. Any kind of data can be sent by HTTP, provided the client and server both know how to handle the data. An HTTP request does exactly what it sounds like, as in it is requesting information/data from a specific server. A basic request, or response, is made up of a header and an optional message body.
Unlike regular HTTP, HTTPS transmits data over an encrypted connection. This is done using Transport Layer Security (TLS) or the older Secure Sockets Layer (SSL). HTTPS allows for the authentication of the website you’re visiting, to make sure it’s actually the site you intend to visit, thus protecting your privacy and the data being exchanged. It also allows you to send data securely across a network.
For more on HTTP and HTTPS, see this explainer article.
HTML
HTML: stands for HyperText Markup Language. Unlike a programming language which uses to perform functions, a markup language like HTML uses tags define types of content and their intended purpose. For example, the headers, texts or tables in a web page are HTML elements. To represent new and less primitive “objects” to the core DOM, programming languages like JavaScript can add, modify, or remove objects using the HTML DOM API. In the analogy to LEGO parts (see DOM), HTML elements can be seen as more “structural” LEGO parts like a person, a car, or a wall, while JavaScript defines the behaviors of those objects, like when they are clicked on, edited, etc.
References:
– Rockey Ke
I
I2C
I2C is a type of synchronous serial protocol. The acronym stands for Inter-Integrated Circuit and its official written form is I2C. is There are only two connections between the controller device and secondary devices. I2C is composed only of a Serial Clock (SCL) connection and a Serial Data (SDA) connection. In an SCL connection, the controller sends the clock signal. In the SDA connection, the controller and secondary devices exchange data in both directions. The figure below shows the connections between a primary device and several secondaries.
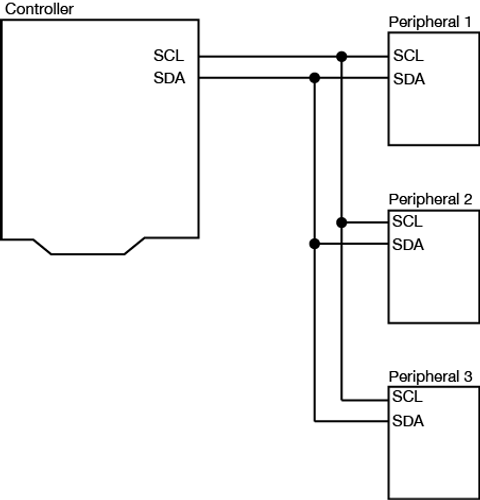
Output of bits is synchronized by a clock signal which is shared by both the primary and secondary devices. The clock signal is controlled by the primary device.
Data is transferred in messages, which are broken up into frames of data, as shown in the Figure below.
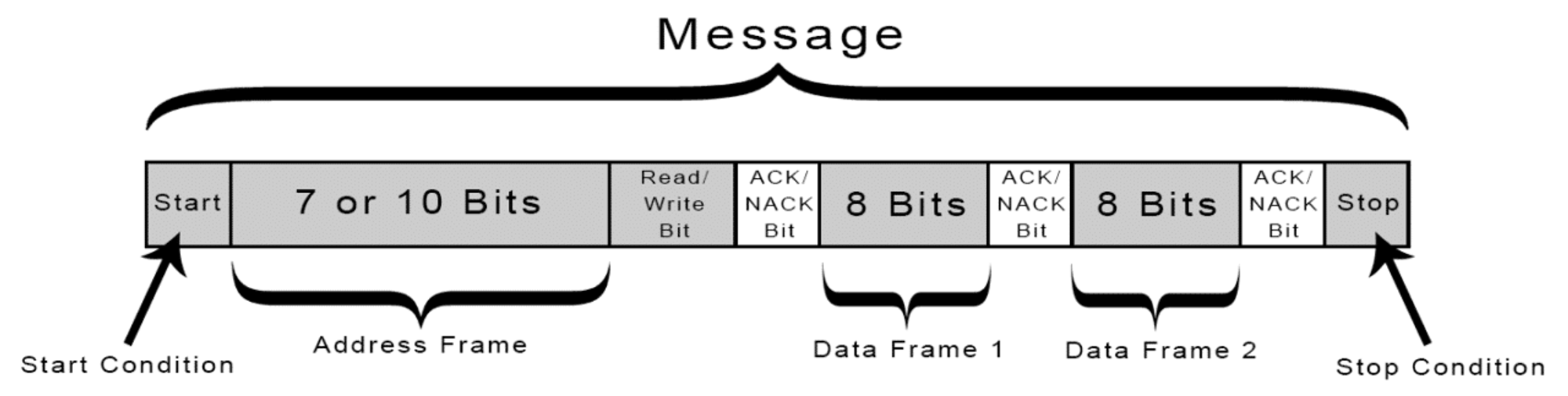
Each message contains:
- start condition: SDA switches from high voltage to low voltage. This occurs before SCL switches from high to low.
- address frame: a sequence of 7 to 10 bits identifying the secondary device to which the primary device talks.
- read/write bit: a single bit which indicates whether the primary device is sending data to the primary device (low voltage) or receiving data (high voltage)
- ACK/NACK bit: stands for acknowledgement/no acknoledgement. This bit indicates whether hte message was sent successfully or not.
- data frames 1 and 2: each data frame is 8 frames long. It is always followed by an ACK/NACK, which must be received before the next data frame is sent.
- stop condition: the SDA line switches from low voltage to high voltage after SCL line switches from low to high.
Serial communication: data is streamed, one bit at a time, over as little as one wire.
References
- I2C explainer from Intro to Physical Computing at NYU
- I2C explainer on circuitbasics.com
- Explainer of serial communication more generally on SparkFun
Note: I have chosen to use the terms “primary” and “secondary” instead of the standard terms “master” and “slave” respectively.
– Martha Janicki
ICE
Interactive connectivity estalishment – An ICE candidate is a public IP address and port that could potentially be an address that receives data. Each user will typically have multiple ICE candidates that are gathered by making a series of requests to a STUN server. It is used as part of the WebRTC protocol.
– Vesper Guo
IMAP
The Internet Message Access Protocol(IMAP) is an internet application protocol that allows email clients to retrieve email messages from a mail server over internet connection from multiple devices.
Comparison of POP3 and IMAP
The design of POP was driven by the need of users having only temporary Internet connections, such as dial-up access, allowing users to retrieve e-mail when connected. It can be only used on one computer, and can’t be synchronized between multiple devices.
IMAP was designed to leave all messages on the server and allow simultaneous access by multiple clients.
Reference:
– Yan Shao
Internet Assigned Numbers Authority (IANA)
Internet Assigned Numbers Authority (IANA): An organization that manages IP address allocation, domain names, and protocol parameters.
– Bianca Gan
Internet Group Management Protocol (IGMP)
IGMP is a communications protocol used by hosts and routers on IPv4 networks to establish multicast group memberships.
Reference: Wikipedia
– Tuan Huang
IP address
An IP address, aka Internet Protocol address, is a label given to every device connected to a network that uses the internet protocol (MDN). It can consist of numbers and/or hexadecimal letters representing the number. The 2 main formats for IP addresses are IPv4 (32-bit) and IPv6 (128-bit). An IPV4 address consists of 4 bytes (32 bits) and an IPV6 address of 6 bytes (128 bits). For example, here is one of Google’s IP addresses:
| Google IPv4 address: |
| 216.58.216.164 |
| Google IPv6 address: |
| 2607:f8b0:4005:805::200e |
Reference:
– Julie Lizardo
J
JavaScript
JavaScript is a programming language that can be used to modify website content elements to make them responsive to a user’s action. The HTML DOM API is a standard for how to get, change, add, or delete HTML elements. JavaScript modifies the objects of the DOM according to its scripted logic. In the LEGO analogy, JavaScript works like the mechanical parts like gears or batteries to make things move.
CSS: stands for Cascading Style Sheets. CSS dictates how the HTML elements of a website should appear on the frontend of the page. CSS communicate with DOM by declaring that it is the style element, and it was applied to HTML elements to finish the look of elements. They are like the paint, color, and facial expression printed on LEGO persons, further articulating their visual characteristics .
JavaScript: JavaScript is a programming language that can be used to modify website content make them responsive to a user’s action. Since the HTML DOM API is a standard for how to get, change, add, or delete HTML elements, JavaScript utilize these function according to its scripted logic. In the LEGO analogy, JavaScript works like the mechanical parts like gears or batteries to make things move, as shown in the Figure below.

References:
– Xiaoyu (Rockey) Ke
K
Kernel
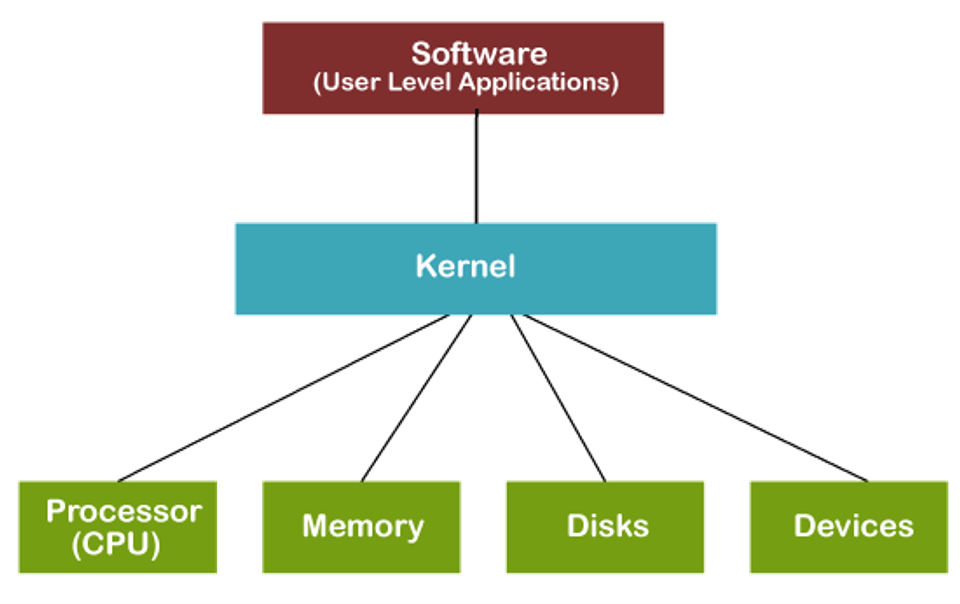
A Kernel is the core of an operating system which constantly performs multitasking from physical hardware to application software. Its goal is to maintain and manages resources by providing access to CPU, memory, disk I/O, and networking as efficient as possible. You can think of the kernel as the main loop of an operating system. The Figure below shows the relationship between the kernel and user software and the hardware of a computer.
References:
- https://www.ionos.com/digitalguide/server/know-how/what-is-a-kernel/
- https://www.digitalocean.com/community/tutorials/what-is-a-kernel
- https://www.javatpoint.com/what-is-kernel
– Erin Tao
Key Pair
Key pair – Two keys, a public key and a private key. See also Cryptography
– Gracy Welihan
L
Local Area Network (LAN)
Local Area Network (LAN) is a group of computers or other IoT devices that are in the same place geographically and share the same physical network.
– Bianca Gan
M
Multicast Domain Name System (MDNS)
mDNS is short forMulticast Domain Name System. It is named as such because it is for sharing IP addresses within small local networks that don’t have their own DNS. When queried to identify itself through mDNS, a machine will multicast a message that any other machine in the subnet can use to identify it. mDNS could be used to connect your computer to your wireless printer, or to use your phone to play Spotify on your gaming console.
References: Ionos.com, multicastdns.org
– Christina Dacanay
MAC Address
Key points –
- identifies a device on a network
- hardware address
- assigned by device manufacturers
A Media Access Control (MAC) address is a string of characters that identifies a device on a network. It’s tied to a key connection device in your computer called the network interface card, or NIC. The NIC is essentially a computer circuit card that makes it possible for your computer to connect to a network. A NIC turns data into an electrical signal that can be transmitted over the network.
Every NIC has a hardware address that’s known as a MAC address. Whereas IP addresses are associated with a networking software called TCP/IP, MAC addresses are linked to the hardware of network adapters.
MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Manufacturers assign a MAC address to a network adapter when it is produced. It is hardwired or hard-coded onto your computer’s NIC and is unique to it. Something called the Address Resolution Protocol (ARP) translates an IP address into a MAC address. Think of the ARP as a passport that takes data from an IP address through an actual piece of computer hardware.
Mac Address Spoofing
MAC spoofing is a technique for changing a factory-assigned Media Access Control (MAC) address of a network interface on a networked device. Changing the assigned MAC address may allow the user to bypass access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another network device. MAC spoofing is done for legitimate and illicit purposes alike.
MAC address spoofing is limited to the local broadcast domain. Unlike IP address spoofing, where senders spoof their IP address in order to cause the receiver to send the response elsewhere, in MAC address spoofing the response is usually received by the spoofing party if MAC filtering is not turned on making the spoofer able to impersonate a new device.
References:
- https://whatismyipaddress.com/mac-address
- ifconfig – https://en.wikipedia.org/wiki/Ifconfig
- https://www.iana.org/assignments/ethernet-numbers/ethernet-numbers.xml
- Identity Masking – https://en.wikipedia.org/wiki/MAC_spoofing#Identity_masking
– Suraj Selvabarathy
Memory stacks and heaps
Memory stacks and heaps – In computer memory, the stack is a temporary area of computer memory that stores the variables created by methods. During runtime, local variables are declared, stored and initialized in the stack. Once the computation is finished, and the variables have been called and used, they will be automatically deleted by the compiler. Stacks have a linear data structure that is in a contiguous block. Refer to heaps for comparison.
The heap is an area of computer memory that stores global variables. Heaps are based on hierarchical structure using trees and arrays. Unlike the stack, de-allocation of variables is not automatic and needs to be specially addressed by the programmer. Also, each block of memory is allocated in random order. Refer to stacks for more comparison.
This is the link to the reference.
– Cy Kim
Multicast
To deliver a packet, there are three kinds of methods –
Unicast, where the packet is sent to a single destination (one-to-one). Broadcast, where the packet is sent to everyone on the network (one-to-all). Multicast, where the packet is sent to a set of hosts that can be on different networks (one-to-many / many-to-many)
The IP Multicast protocol is a method for one-to-many and many-to-many real-time communication over an IP infrastructure, sending datagrams* to a group of interested receivers in a single transmission. It is commonly used in applications such as online streaming video and gaming.
Key concepts in IP multicast include an IP multicast address, a multicast distribution tree and receiver driven tree creation. To join the multicast group as a receiver, it uses the IGMP protocol.
For an IP multicasting to work, on the data link layer (Ethernet) you need a multicasting MAC address to identify a host’s network interface hardware, and a multicasting IP group address on the network layer (IP) for the computer to receive the multicast message and see it as a multicast datagram. These two addresses (IP address and MAC address) are mapped to each other through a specific calculation.
With the addresses mapped to each other, the multicast process happens as follows: A hardware with receive a multicast datagram on a multicast MAC address. It strips the MAC addresses off and send the rest to the above layer, which is the Network Layer. At that point, the Network Layer needs to be able to understand it’s dealing with a multicast, so the IP address is set in a way that allows the computer to see it as a multicast datagram.
Reference:
– Tuan Huang
N
Network Latency
Key points –
- delays in communication over a network
- low (latency) is good and high (latency) is bad
Network latency, or lag, is the term used to describe delays in communication over a network. In networking, it is best thought of as the amount of time taken for a packet of data to travel through multiple devices, then be received at its destination and decoded.
Low latency is good, meaning there is little or no delay.
High latency is bad, meaning it takes a long time for the requested resource to reach its destination.
Long delays that occur in high-latency networks create bottlenecks in communication. In the worst cases, it’s like traffic on a four-lane highway trying to merge into a single lane. High latency decreases communication bandwidth, and can be temporary or permanent, depending on the source of the delays.
References –
- https://www.ir.com/guides/what-is-network-latency#anchor1
- https://developer.mozilla.org/en-US/docs/Glossary/Latency
- https://en.wikipedia.org/wiki/Network_delay
– Suraj Selvabarathy
NAT
Network Address Translation – is a service that operates on a router or edge platform to connect private networks to public networks like the internet. For instance, you can can install a software with a NAT device to a server that sits in the private subnet, which has no internet access directly.
– Vesper Guo
O
OCSP
OCSP – Online Certificate Status Protocol is used in the handshake of setting up an SSL connection. When visiting a secure website a user’s browser sends a OCSP request to a CA (Certificate Authority) to confirm if the certificate is valid. Specifically checking the revocation status of a X.509 digital certificate.
– Jake Sherwood
Octet
An ‘octet‘ and a ‘byte’ are essentially the same thing ( 8 bits of data ). However, the term ‘octet’ is used mainly within the context of networks.
OSI
The Open Systems Interconnect (OSI) model defines telecommunications networking in terms of a vertical stack of seven layers. Upper layers of the OSI model represent software that implements network services like encryption and connection management. Lower layers of the OSI model implement more primitive, hardware-oriented functions like routing, addressing, and flow control.
Data communication in the OSI model starts with the top layer of the stack at the sending side, travels down the stack to the sender’s lowest (bottom) layer, then traverses the physical network connection to the bottom layer on the receiving side, and up its OSI model stack.
- Layer 1: Application Layer
- Layer 2: Presentation Layer
- Layer 3: Session Layer
- Layer 4: Transport Layer
- Layer 5: Network Layer
- Layer 6: Data Link Layer
- Layer 7: Physical Layer
References:
- Wikiedia’s page on the OSI model
- A nice comparison of the OSI and TCP/IP stack models.
Open Sound Control (OSC)
Open Sound Control or OSC – see this explanation.
P
Packet
Packet: In networking, a packet is a small segment of a larger message. Data sent over computer networks, such as the Internet, is divided into packets. These packets are then recombined by the computer or device that receives them.
The structure of the network packet consists of three parts; header, payload, and trailer. The header includes instructions about the data carried by the packet. The payload is the body of a packet, which is the actual data that the packet is delivering to the destination. Finally, the trailer contains a couple of bits that tell the receiving device that it has reached the end of the packet.
Reference:
https://www.cloudflare.com/learning/network-layer/what-is-a-packet/
– Sihan Zhang
Packet vs. Frame
- Network layer: This layer organizes and transmits data between multiple networks.
- Data link layer: This layer concerns data transmission between the nodes within a network and manages the connections between physically connected devices such as switches.
Framing is used in a point-to-point connection between two computers or between a computer and a router. Data is transmitted as a stream of bits. The frame header contains the source and destination MAC addresses. When a router receives a frame from one computer, it will compose another frame with the content of the first frame but update the source MAC address.
There are two types of frames: fixed-length and variable-length frames. In fixed-length framing, the size of the framework is the delimiter; if you know the frame size, you know how many bytes to count until the end of the frame. So there is no need to set a boundary for the frame. In variable-length framing, it’s difficult to determine the start and end of a frame, so it’s essential to define the start and end of a frame.
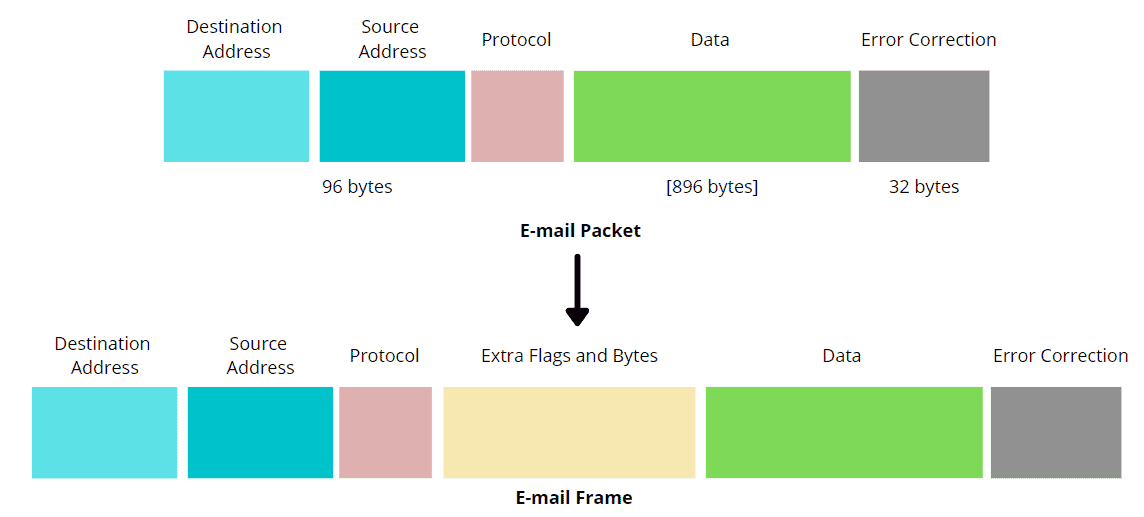
Figure. The parts of an Ethernet Frame. Image credit: https://www.baeldung.com/cs/networking-packet-fragment-frame-datagram-segment
References:
- https://www.bmc.com/blogs/osi-model-7-layers/
- https://www.baeldung.com/cs/networking-packet-fragment-frame-datagram-segment
– Jingyuan Li
Packet header
Data sent over computer networks, such as the internet, is divided into packets. A packet header is a “label” which provides information about the packet’s contents, origin, and destination. Network packets include a header so that the device that receives them knows where the packets come from, what they are for, and how to process them.
Packets actually have more than one header and each header is used in a different part of the networking process. Packet headers are attached by certain types of networking protocols. At a minimum, most packets that traverse the internet will include a Transmission Control Protocol (TCP) header and an Internet Protocol (IP) header.
For example, the IPv4 packet header consists of 20 bytes of data that are divided into the following fields:
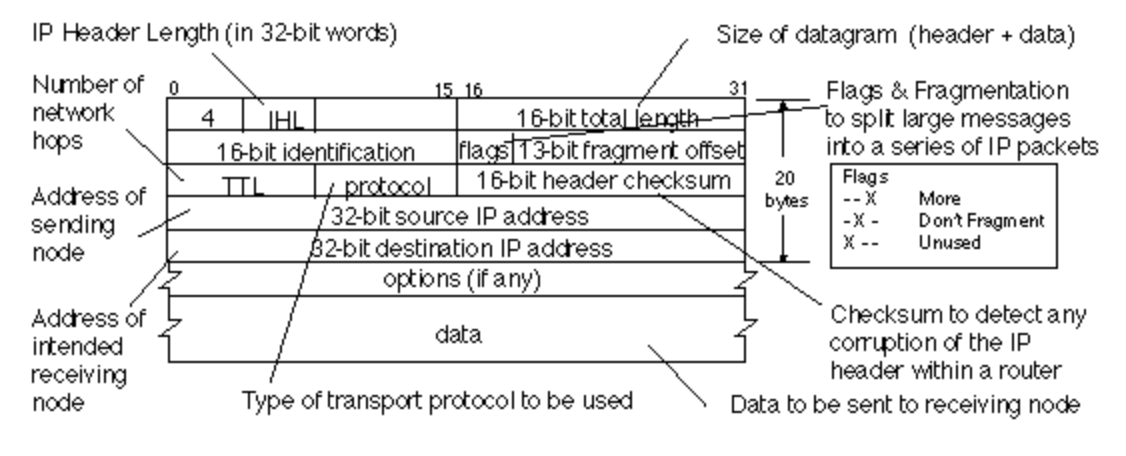
References:
- https://www.cloudflare.com/learning/network-layer/what-is-a-packet/
- https://erg.abdn.ac.uk/users/gorry/course/inet-pages/ip-packet.html
– Priyanka Makin
Packet Switching
When a host wants to send data to another host through the internet, the data (e.g. a video, audio, picture, text, etc) will split into smaller chunks of data which are called packets. The packet will be received by a router which will then send it to the destination host. At the destination, all these small chunks (packets) have to be reassembled to recreate the data.
The router receives the whole packet and pass it to the next router or the host. This is called store-and-forward transmission. Dividing a file into packets helps to raise the efficiency of network transformation, because it allows the router to receive and send the packet at the same time, and to send different packets via different routes, if one route becomes congested mid-transmission. More than one user, application, and/or node may take turns sending and receiving data through a router without permanently retaining the underlying medium/channel, as in a circuit-switched network.
Reference:
Packet switching | Packet switched network | Switching technology | TechTerms (YouTube video)
– Jingyuan Li
PEM
PEM stands for Privacy Enhanced mail, and was originally intended for use to secure email communication through the internet, but has since become a standard for internet security. It is used as a file type in Public Key Infrastructure (PKI)*, as a file format that stores cryptographic keys, such as SSL certificated along with their associated private keys.
A PEM file is created in four steps.
- The email message is converted into a standard depending on the operating systems of the sending and receiving parties.
- The message digest* of the email in addition to the sender’s private key is then encrypted together to create a digital signature, as shown in the figure below.

- Then the message digest along with the digital signature is encrypted with the symmetric key to create the encrypted message, as shown in the figure below.

Lastly the binary encrypted message goes through base-64 encoding* process that outputs a message containing characters.
References:
- Also see, VPN: Beginner’s Guide
- What Are PEM Files?
- Privacy Enhanced Mail (PEM) and Its Working
- What Is A PEM File? And How Do You Use It?
– Bianca Gan
Pointer
A pointer is a variable that stores the memory location of data. Using pointers helps improve performance by reducing repetitive operation (copying and accessing data).
references:
- https://en.wikipedia.org/wiki/Pointer_(computer_programming)
- https://beginnersbook.com/2014/01/c-pointers/
- http://lidia-js.kis.p.lodz.pl/ITCS/theory/CPointers.php
–I-Jon Hsieh
PKTGEN
PKTGEN – Is a Linux kernel tool for generating packets. In addition to being a tool PKTGEN is a protocol used to define the format of the test packets. It is typically used for testing and measuring latency, packet arrival and delay, throughput and other user defined rates.
– Jake Sherwood
Private Key
Private Key – A long randomly (or pseudo-randomly) generated sequence of bits that cannot be easily guessed. It is only known by the generator/originator and can encrypt and decrypt data. The complexity and length of a private key determines how secure it is. Private keys are stored in the software or operating system you use.
See also Cryptography
– Gracy Welihan
Public Key
Public Key – A key that can be exchanged with anybody and is freely shared to anyone. It is used to encrypt messages for a specific recipient with the matching private key. Public keys are stored on digital certificates for secure transport and sharing and can be published on the internet.
See also Cryptography
– Gracy Welihan
POP
The Post Office Protocol(POP) version 3(POP3) is an application layer protocol provides an email client to retrieve email messages, store on the client computer, and delete them from the server.
Reference:
– Yan Shao
Protocol
A communication protocol is a system of rules in telecommunications that allow two or more entities to transmit information to each other. A protocol can be implemented in hardware, software, or a combination of both.
Reference: Wikipedia’s page on protocols
Proxy Server
A proxy server is a middleman between client (you) and server (the web). It functions as a firewall and web filter, provides shared network connections, and speeds up common requests by caching data. Proxy server provides high level of privacy since it can hide your IP address when you do any request, and encrypt your data for secure transition, and can block access to certain web pages based on IP address.
Reference:
– Yiting Liu
Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI): Is the system of using a private and public key for encryption
– Bianca Gan
Q
QUIC
QUIC is a low-latency Internet transportation protocol designed by Google in 2012. Combining features from TCP and UDP, it aims to reduce latency primarily by improving two behaviours of HTTP traffic.
First, it simplifies the process of secure connection setup, combining together multiple steps into a single request-response. On the other hand, using UDP as its basis, QUIC is inherently a lighter weight transmission protocol, but it also involves some TCP features such as congestion control and loss recovery. Meaning data are streamed through UDP, and if single packets are loss, they could be checked and retransmitted by QUIC individually. This allows data to flow freely even when error occurs and all of its data wouldn’t be blocked.
In short, QUIC allows the transmission to have the speed and efficiency of a UDP connection, while having the security and accuracy of a TCP connection.
Reference:
– Tuan Huang
R
Regular Expressions (regex)
Regular Expressions, or regexes, are “specially encoded text strings used as patterns for matching sets of strings.” (Fitzgerald). When you’re using a search tool, sometimes you want to search for patterns of text rather than a specific text. Here are a few examples of regular expression patterns:
- ^ – the start of a string, or start of a line in multi-line text
- $- the end of a string, or end of a line in multi-line text
- \s – any whitespace character (spaces, tabs, linefeeds, etc)
- \S – any character that’s not whitespace
- \d – any numeric (digit) character
- \D – any character that’s non-numeric
- \w -any word character (letters or numbers, but not punctuation or whitespace)
- \W – any non-word character
- \x – any hexadecimal digit (0-9 and a-f or A-F)
Regular expressions can be combined to create complex searches. For example, perhaps you want every day in the month of August, formatted like this: “August 23”. You’re searching for the word “August” followed by one or more spaces, followed by one or more numeric characters. The regular expression might be August\s+\d+ . Or if you’ll take any word that starts with “Aug”, followed by any whitespace or punctuation, it would be Aug\w[\s|\W*]\d+. This pattern would match “August 23”, “Aug 23”, “Aug-23”, or “Aug.23”, or any other numeric date in August.
Regular expressions have been used in programming as patterns for text searches for decades, and despite the name, there are some variations in the patterns. Different programming engines use slightly different variations on regular expression patterns. There are numerous guides and cheat sheets to regular expressions available on the web. When you’re looking for one, it helps to search for the context in which you want to use them, for example “regular expressions in JavaScript” or in C/C++, or in Python, or on the Linux command line, and so forth.
Here are a few useful regex explainers and cheat cheets:
- Introducing Regular Expressions online book by Michael Fitzgerald (O’Reilly)
- regexpal, a regular expression tester
- Using Grep & Regular Expressions to Search for Text Patterns in Linux by Justin Ellingwood and Brian Hogan (Digital Ocean)
- Mozilla Developer Network (MDN) regular expression syntax cheat sheet
- Regular-Expressions.info
- Regular Expressions Cheat Sheet by DaveChild
REST
REST – REST stands for Representational State Transfer. It’s an architectural style for developing web systems, though it is also used in other systems like OSC and MQTT.It was first theorized by Roy Fielding in his 2000 Ph.D dissertation . Web servers provide HTTP endpoints that return data formats like JSON or CSV are referred to as REST APIs For more on REST, see:
- REST explainer by Youming Zhang
- Understanding REST
- Building Web Services the REST way
Routing
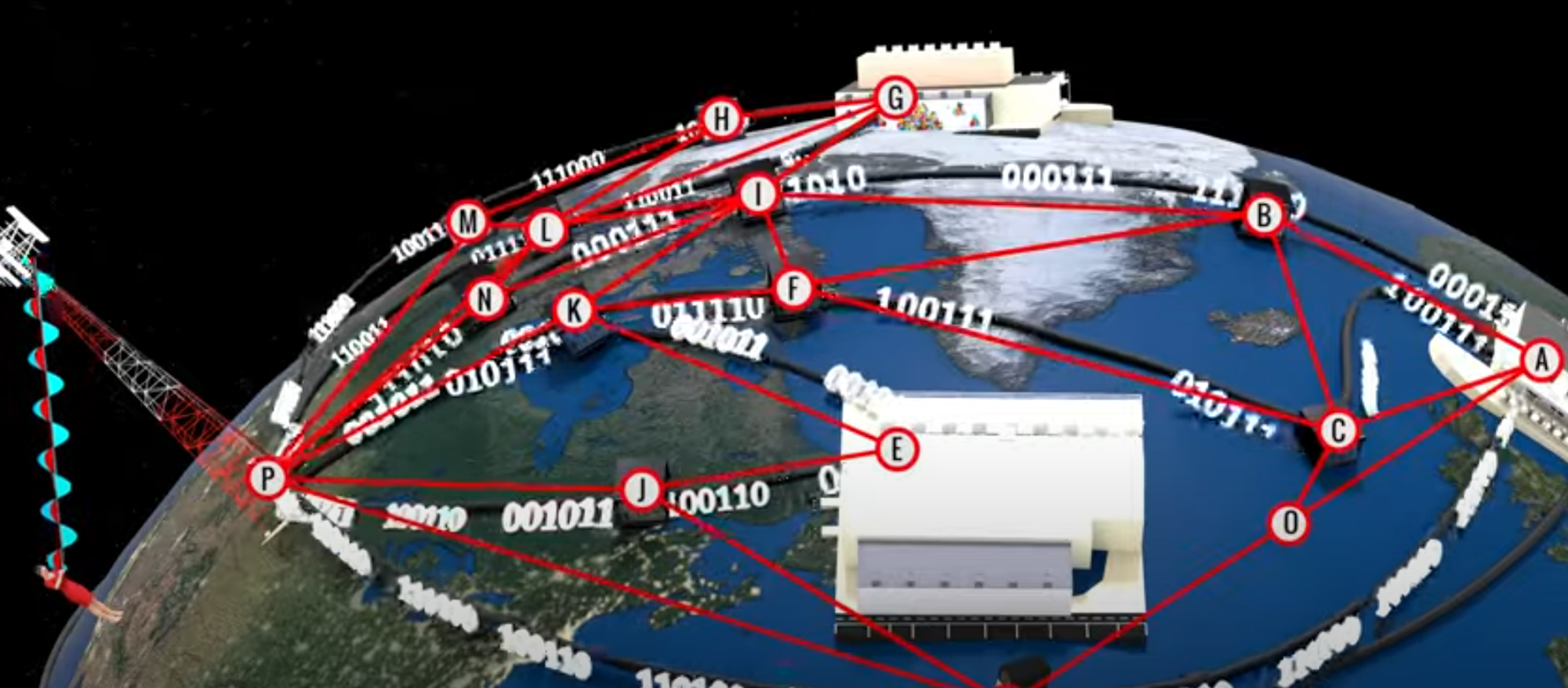
Routing is the process by which packets are transported from the source to the destination through routers in between the two. The route that a packet takes depends on the state of the network and routers. Routers will plan the shortest route time from their location to the destination based on traffic conditions.
A router is a device that connects two or more packet-switched networks or subnetworks. It serves two primary functions: managing traffic between these networks by forwarding data packets to their intended IP addresses, and allowing multiple devices to use the same Internet connection.
Source: Cloudflare, “What is a router?“
There are two types of routing: Static & Dynamic. Static routing is programmed into routers manually. Therefore, if a connection breaks between a given router and other routers on the route, the packet cannot reach the destination.
In Dynamic routing, the routing is set by each router’s routing table and the decision of which route to take depends on what the router knows of the current network state. One of the most common routing algorithms, Dijkstra’s algorithim, was created and published by Dr. Edsger W. Dijkstra. It aims to find the shortest path from one node to another.
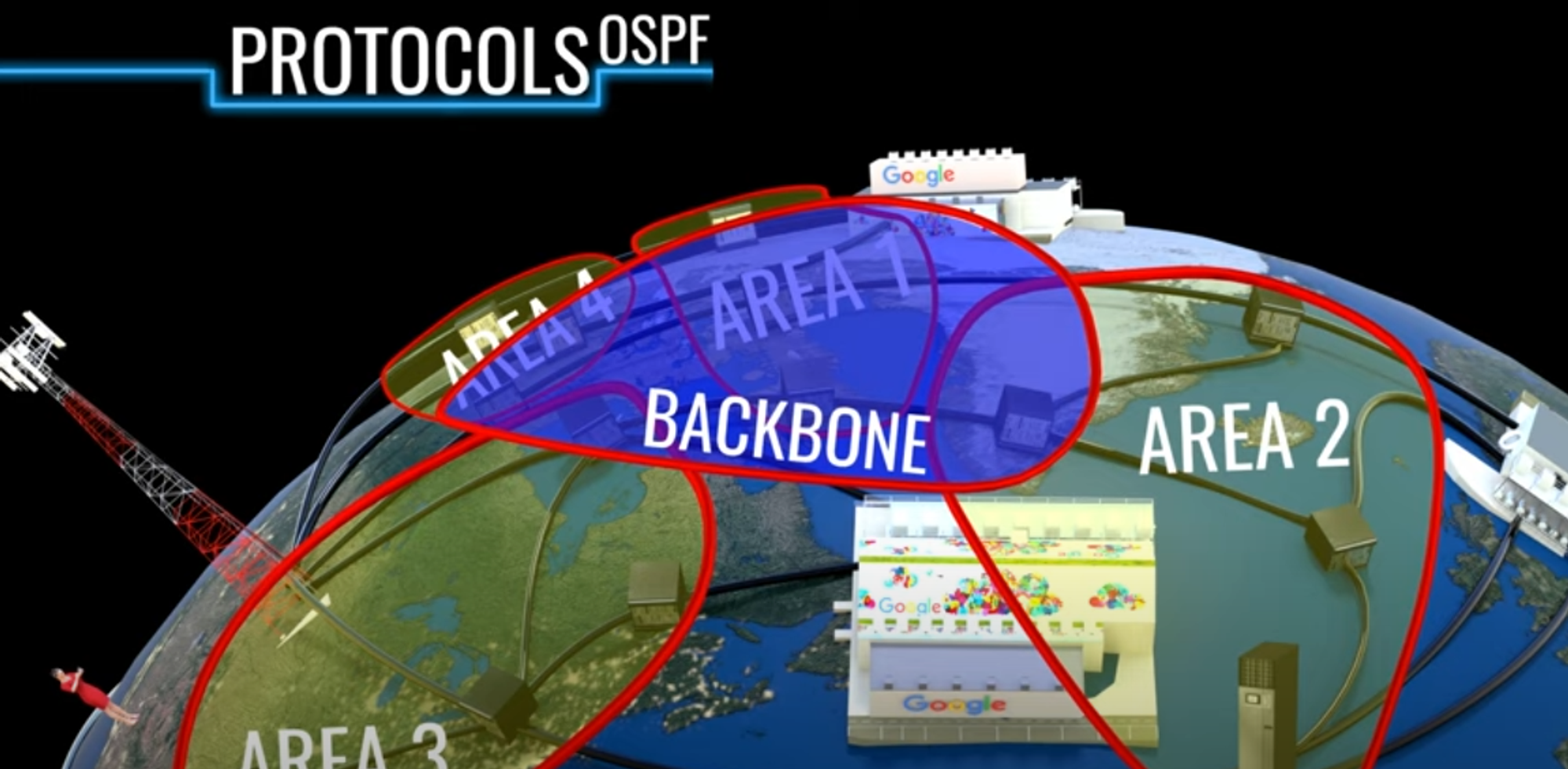
We could see from the figure below, the network is divided into different areas and one backbone area which shares at least one router from local areas. These routers are called border routers. If the packet needs to transfer to another local area, they have to go through a backbone area.
References:
- https://www.freecodecamp.org/news/dijkstras-shortest-path-algorithm-visual-introduction/
- Understanding Routing! | ICT#8 (YouTube)
- https://www.cloudflare.com/learning/network-layer/what-is-a-router/
- https://en.wikipedia.org/wiki/Open_Shortest_Path_First
– Jingyuan Li
RSA
RSA is short for Rivest–Shamir–Adleman, the name comes from the combined surnames of its creators. It is an asymmetric encryption algorithm for secure data transmission widely used in many products and services. It differs from AES in that it uses a public-key cryptosystem which the encryption and decryption works on two different keys, a public key and private key. For example, a client sends its public key (accessible to anyone) to the server to request some data, and this data will be encrypted by the server using the public key that the client sent, finally the client received this data and decrypt it with the private key (only the client knows).
In RSA, the public key is generated by multiplying two large prime numbers p and q together, and and the private key is generated through a different process involving p and q. Then the user A can distribute his public key, which is pq, and if another user wishes to send message to user A, they can encrypt the message using pq.
The implementation of RSA makes heavy use of modular arithmetic, Euler’s theorem, and Euler’s totient function (also known as the Phi function), but overall the idea of RSA is to utilize the difficulty of prime factorization, and RSA keys commonly tend to be 1024 or 2048 bits in length. Therefore the longer an RSA key, the more secure it is.
See also Cryptography.
References:
- https://www.geeksforgeeks.org/rsa-algorithm-cryptography/
- https://www.youtube.com/watch?v=ZPXVSJnDA_A
- https://www.encryptionconsulting.com/education-center/what-is-rsa/
- https://brilliant.org/wiki/rsa-encryption/
– Erin Tao
S
Server
A server is software or hardware that provides resources, data, services, or programs to other computers (called clients) over a network. This structure is called the client-server model. In theory, whenever computers share resources with client machines they are considered servers. This can include the most advanced computers right down to the most simple (microcontrollers). Any networked device that can share resources is acting as a server.

Server hardware consists of physical devices that are responsible for holding data. They include all internal server components, including processors, chassis, network cards, memory, hard drives, storage and power supplies. The figures below show typical server rooms featuring rows of hardware in racks.


Server software is a type of software that is designed to be used, operated and managed on a computing server. Server software is primarily built to interact with a server’s hardware infrastructure, including the processor, memory, storage, input/output (I/O) and other communication ports. Depending on the type or usage of the server, server software may be classified into various forms, such as the following:
- Web server software
- Application server software
- Database server software
- Cloud computing server software
- File server software
Each of the above types of server software utilizes the server for different functions and services, but all focus their primary objective on using inherent computer capacity and resources. Moreover, server software may be for a physical or virtual/cloud server built on a physical server.
References:
- Why is server monitoring important?
- Server(Computing)
- Types of server hardware
- Serversoftware
- What is a Virtual Private Server (VPS)?
– Michelle Xu
SMTP
Simple Mail Transfer Protocol(SMTP) is a connection-oriented, text-based internet communication protocol for sending and receiving emails.
In the SMTP process model, an email is submitted by a mail client (mail user agent, 0r MUA) to a mail server (mail submission agent, or MSA), typically on TCP port 587 (formerly on port 25). The MSA delivers the mail to its mail transfer agent(MTA). Mail Transfer Agents (MTAs) transfer messages between each other using SMTP.
User-level email clients typically use SMTP only for sending messages, and uses IMAP or POP3 for retrieving messages.
References:
- Wikipedia: Simple Mail Transfer Protocol
- Postmark: Everything you need to know about SMTP (Simple Mail Transfer Protocol)
– Yan Shao
SSID
A WiFi network’s Service Set Identifier ( SSID ) is commonly referred to as the network name. When you’re selecting a network to join, the names you see are the SSIDs of all the available networks. These names are associated with an 802.11 WLAN (Wireless Local Area Network). 802.11 is just a generic name of a family of standards for wireless networking related to Wi-Fi. Client devices, like your computer or smartphone, use this SSID to identify and join wireless networks. Routers broadcast this name to help wireless clients find the network. For more on WiFi see this explanation of WiFi and this explanation of the 802.11 protocol.
SDP
Session description protocol – it is an object that contains information about the session connection such as the codec, address, media type, and so on. Both peers will exchange SDP’s so they can understand how to connect to each other. One in the form of an SDP Offer and another as an SDP Answer.
SIP
Session Initiation Protocol is the protocol of the application layer. It runs on UDP or TCP. SIP describes the way to establish Internet telephone calls, video conferences and other multimedia connections, manage them and terminate them. It can establish two way party session, multiparty session and even multicast session.
In SIP, the sender and receiver are often identified by an email address, an IP address, or a phone number.
SIP uses messages in ASCII text; each message features a header and a body; the message types includes ACK (acknowlegement) as mentioned before.
SIP requires a three-way handshake: The caller sends an INVITE message. The callee then sends back a reply message. To verify that a reply code is received, the caller sends an ACK message. After the session is established, the caller and callee communicate using two temporary ports. To terminate the session, either caller or callee can send out a BYE message.
Streaming
Streaming refers to the continual transmission of audio and video files from a server to a client. Just like other data that’s sent over the Internet, audio and video data is broken down into packets. Each packet contains a small piece of the file, and an audio or video player in the browser on the client device takes the flow of data packets and interprets them as video or audio. Some streaming methods use UDP, and some use TCP. UDP is used when speed takes precedence over reliability, while TCP is used when reliability takes precedence.
– Sihan Zhang
STUN
Session Traversal Utilities for NAT – it defines a systematic way of finding possible communication options between a peer and the Video Gateway (WebRTC). It allows clients to discover their public IP address and the type of NAT they are behind.
Socket
Socket (TCP) A connection between two computers uses a socket. TCP socket is a connection-oriented socket that uses the Transmission Control Protocol. TCP socket is defined by the IP address of the machine and the port it uses: the IP address identifies a specific network destination; the port number identifies the specific application or service on that device to connect to. The combination of IP address and the port is called an endpoint.
For instance, we have our browser open, trying to connect to the website at IP address 8.8.8.8 at its port number 80 (a well known one). By doing this, we are sending an HTTP request from our client at IP address 120.1.1.1. with port number 3022 for the web browser. In this scenario, the server socket is 8.8.8.8:80, and the the client socket is 120.1.1.1:3022. The overall connection between these two can be described using this socket pair: (8.8.8.8:80, 120.1.1.1:3022).
Unlike UDP which doesn’t need a connection, the TCP socket guarantees that all data is received and acknowledged.
Note that TCP socket is not the same as Websocket, though the Websocket protocol is based on TCP socket.
- reference
– Vesper Guo
Symmetric Encryption
Symmetric Encryption – Uses one distinct private key to encrypt and decrypt messages. Both the sender and receiver use the identical key when communicating with each other. With Symmetric Encryption everyone you want to communicate with needs a distinct key and you must manage all of those keys.
Symmetric Encryption is nice and simple and it works, but both parties need to know what the key is, need to agree on a key that nobody will be able to guess, and have to share it with one another. This can be hard to do safely unless people are physically in the same place or requires extra communications overhead using something like the Deffie-Helman Key Exchange.
See also Cryptography, AES
– Gracy Welihan
T
TCP
Transmission Control Protocol (TCP) and Internet Protocol (IP) are two distinct computer network protocols. TCP and IP are commonly used together and are often simply referred to as TCP/IP. IP forms part of the Network layer in the OSI model, whereas TCP forms part of the Transport layer.
TCP/IP technically applies to network communications where the TCP transport is used to deliver data across IP networks. Being a “connection-oriented” protocol, TCP works by establishing a virtual connection between two devices via a series of request and reply messages sent across the physical network.
Traceroute
What is Traceroute? Traceroute is a command line tool which can be used to trace the path that packets take to reach a destination through networks. It examines how data moves through the Internet by showing how packets hop from one stop to another along the route. It is useful for diagnose problems in computer networks.
How does Traceroute work? Traceroute works by sending packets with a short time-to-live (TTL) to routers involved in transferring the data. When these packets expire, the routers will produce a message that identifies themselves. Traceroute will then return these messages to the sender, and thus revealing the hops in the route.
Pros and cons
- Pros:
- Every router is able to send TTL exceeded messages. Therefore, no special code is required for that.
- Cons:
- The number of packets generated in the process is twice the number of routers.
- The path may change during the process.
- The return path is not traced, which may be different from the outbound path.
References
- Original source: https://www.rfc-editor.org/pdfrfc/rfc1393.txt.pdf (developed in 1993)
- https://www.cloudns.net/blog/traceroute-command-tracert/#What_is_the_Traceroute_command
- https://www.varonis.com/blog/what-is-traceroute
- https://www.fortinet.com/resources/cyberglossary/traceroutes
- https://www.digitalocean.com/community/tutorials/how-to-use-traceroute-and-mtr-to-diagnose-network-issues
– Lily Yu
U
UDP
UDP stands for User Datagram Protocol. It is a data transport protocol. To send some data via UDP, all that is required is a destination port and IP address. When using UDP your data is wrapped into a “packet” with a header that indicates the destination address and some other information, and then you send out the packet.
UDP is fast and lightweight. As a compromise, it does not provide any feedback on the status of the packet after it has been sent. Neither does it guarantees that the packets you send to another host will arrive in the order that they were sent. Therefore, UDP is sometimes known as the Unreliable Data Protocol.
UDP and TCP are the two dominant protocols that computers use to communicate in today’s networks.
The difference between UDP and TCP is that TCP (Transmission Control Protocol) sends data with extra information embedded in the packet headers to help the protocol track the packets it has sent. When a computer receives a TCP packet, it sends back a small acknowledgement packet to the compuer that sent the packet. This allows the TCP to track which packets have been received successfully by the sender. If an acknowledgement (ACK) packet is not received within a certain time of sending a packet, the packet is re-sent. Because each packet is labelled in a timingly manner, the TCP on the receiving computer is able to sort the incoming packets into the proper order even if they were received out-of-order.
To think about their difference in short:
- UDP is a one-way communication, fast but might lacks accuracy and certainty;
- TCP is a two-way communication, its data delivery is more stable and accurate.
– Vesper Guo
URL
URL, or Uniform Resource Locator, is an address to where a specific resource lives on the web. It works in the same way that your home address dictates where you live in your neighborhood.
The basic anatomy of a URL consists of 8 main parts. Take, for example, the URL:
http://www.example.com:3000/path/resource?id=123#section-id
It can be broken into the following parts:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
http:// | www. | example. | com | :3000/ | path/resource | ?id=123 | #section-id |
- Scheme – refers to the protocol. It is the set of rules the browser must use to access and exchange data on the web. The 2 most common protocols for websites are HTTP and HTTPS, but there are many others.
- Subdomain,
- Domain, and
- Top-level Domain – These 3 parts make up what is generally known as the domain name. Computers need to constantly communicate with each other to perform various actions. All devices connected to the internet have a unique identifier that consists of a series of numbers and letters called an IP Address. Since IP addresses can be long and hard to remember, domain names were made so that websites could be easier to type and access.
- Port – indicates what door a browser should use when it arrives at a resource’s location (MDN)
- Path – provides a more specific location to a specific resource
- Query String – allows users to communicate and send small amounts of data to the server side
- Fragment Identifier- is a an anchor. It identifies a specific location on a HTML page.
References:
- https://developer.mozilla.org/en-US/docs/Learn/Common_questions/What_is_a_URL
- https://www.verisign.com/en_US/website-presence/online/what-is-a-url/index.xhtml
- https://blog.hubspot.com/marketing/parts-url
See also A Gentle Introduction to HTTP by Maria del pilar Gomez ruiz
– Julie Lizardo
V
Virtual Private Server (VPS)
A VPS is basically a server running within a server. One physical server hosts multiple virtual servers, each isolated from the others. This is accomplished with software, called a hypervisor, that segments the physical server and keeps each segment separate from the rest.
Traditional servers dedicated one computer and its operating system to running one server program. Multiple users might be allowed access to that server, as the server program was performing the same service for them all (e.g. an HTTP server like nginx serving everyone’s content from different user directories). Since that is wasteful of hardware and energy, and a potential security risk, virtual private servers were created in response. A VPS is a software instance of all of that.
References:
- Why is server monitoring important?
- Server(Computing)
- Types of server hardware
- Serversoftware
- What is a Virtual Private Server (VPS)?
– Michelle Xu
VLAN
VLAN stands for virtual local area network. It is a layer in a network that groups devices together that share a physical LAN* (a group of computers or other IoT devices that are in the same place geographically that share the same physical network), which groups the traffic of these devices.
Main reasons to implement VLANs is to improve performance of some devices, as an organization tool for many devices, tighten security, ease administration in a network. By grouping traffic of some devices, this reduces the traffic going through one device in order to improve its performance. Grouping certain devices together, can also give people control of the access devices have to one another. And in an administration example, devices that can be grouped together in a logical form, i.e. all security devices on one VLAN, all accounting devices on another.
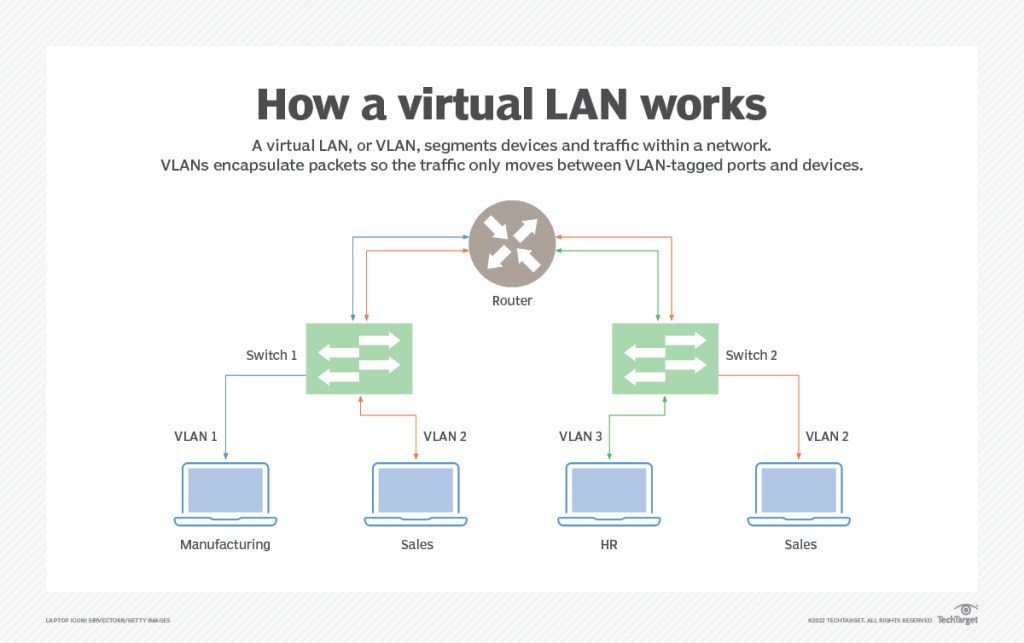
VLANs work by assigning /inserting an ID to the header data of an Ethernet Frame incoming through a network switch. Network switches can then pass through these tagged frames to their associated destination.
Resources:
– Bianca Gan
Virtual Private Networks (VPN)
Virtual Private Networks – see this explanation.
VoIP
Key points –
- used for delivery of voice messages over the internet
- digital transmission
- cost efficient
- facetime audio, whatsapp audio, skype audio
Voice over Internet Protocol (VoIP), also called IP telephony and broadband telephony, is a group of technologies for the delivery of voice messages and multimedia sessions over the Internet. It lets users make and receive phone calls over the Internet instead of the traditional landline Public Switched Telephone Network (PSTN.)
Everything transferred through VoIP is digital. The main reason for using VoIP technology is because of cost. Usually, telephone calls over the Internet do not incur further charges beyond what the user is paying for Internet access, much in the same way that the user doesn’t pay for sending individual emails over the Internet.
Quality of VoIP
Communication on the IP network is perceived as less reliable in contrast to the circuit-switched public telephone network because it does not provide a network-based mechanism to ensure that data packets are not lost, and are delivered in sequential order. Voice, and all other data, travels in packets over IP networks with fixed maximum capacity. This system may be more prone to data loss in the presence of congestion than traditional circuit switched systems; a circuit switched system of insufficient capacity will refuse new connections while carrying the remainder without impairment, while the quality of real-time data such as telephone conversations on packet-switched networks degrades dramatically. Therefore, VoIP implementations may face problems with latency, packet loss, and jitter.
Network routers on high volume traffic links may introduce latency that exceeds permissible thresholds for VoIP. Excessive load on a link can cause congestion and associated queueing delays and packet loss. This signals a transport protocol like TCP to reduce its transmission rate to alleviate the congestion. But VoIP usually uses UDP not TCP because recovering from congestion through retransmission usually entails too much latency.
References –
- https://developer.mozilla.org/en-US/docs/Glossary/VoIP
- https://en.wikipedia.org/wiki/Voice_over_IP#India
- PSTN – https://en.wikipedia.org/wiki/Public_switched_telephone_network
- https://www.fcc.gov/general/voice-over-internet-protocol-voip
– Suraj Selvabarathy
W
WebSockets
The WebSocket API, or Websockets, is a communications protocol that establishes a persistent, two-way connection between a user’s browser and a server. The connection is run over a single TCP connection, and with this API, messages and event-driven responses can be sent and received without having to poll the server for a reply. The protocol uses HTTP as the first transport mechanism but then switches to a bidirectional binary protocol when the WebSocket connection is established. This allows for ‘real-time’ applications and is distinct from HTTP, which is strictly unidirectional.
For a more detailed explanation, see this explanation.
Sources:
https://developer.mozilla.org/en-US/docs/Web/API/WebSockets_API
https://en.wikipedia.org/wiki/WebSocket
https://medium.com/@tfarguts/websockets-for-beginners-part-1-10796106e207
https://sookocheff.com/post/networking/how-do-websockets-work/
– Emily Zhao
WebRTC
WebRTC stands for Web Real-Time Communication. It is an open-source project that allows us to add real-time communication capabilities to our web applications via application programming interfaces. The technologies behind WebRTC are implemented in all major browsers as JavaScript APIs. With WebRTC, we can do things like streaming audio and video content to other people on the browser by allowing direct peer-to-peer communication, without the need to install plugins or download native apps.
WebRTC uses UDP and it doesn’t rely on a server for data flow like websocket does. However, WebRTC does require third-party signaling services, like websockets, to begin with. This is a process called signaling, where peers are brought into a channel or room to exchange session description protocol (SDP) and ICE candidates in order to build a connection.
The two peers exchange their SDPs to get connected first, but they can yet to transmit data. To proceed, they need to ‘find’ the optimal path for the data to flow — this is because most devices sit behind firewalls and NAT devices nowadays, so peers have to coordinate the discovery of their public IP addresses, and this is a process called ICE, Interactive Connectivity Establishment.
When exchanging SDP, a series of requests are sent to a STUN server which will generate a list of ICE candidates. When peer A gets these ICE candidates back from the server, they will send them over to peer B; the network will then determine the best candidate to use. Peer B will do the same vice versa. When the candidates are exchanged, a path is discovered between the two peers and now they can start a data flow in between.

WebRTC, like SIP (Session Initiation Protocol), is a VoIP (Voice over Internet Protocol) technology and it integrates SIP functionality.
We have learned that WebRTC has a premise of establishing a session before one can communicate with another peer. The function of SIP lies in this process of setting up a session — SIP operates on a session, finds the other user, sets up the session, manages the session, and ends the session.
While WebRTC requires SIP, SIP doesn’t rely on WebRTC because SIPs can use multimedia systems on a computer without a browser. For example, users can use SIP with a VoIP provider and softphone software. However, WebRTC makes SIPs easier to use since it works on a browser, so that we don’t need to download an app for the communication.
- reference
– Vesper Guo
Terms Yet to be Defined
MIME
Port forwarding – taken
telnet – taken
datagram
chunk
NAT
UTF – taken
netcat – taken
NTP – taken
Runtime – taken
SSH – taken
SSL – taken
DMX – taken
Serial (Uart) – taken
ASI – taken
event loop – taken
peer-to-peer – taken
REPL (read-eval-print)
Async – taken
Blob – taken
Blocking vs. non-blocking
Twos complement – taken
Kernel
hashtable – taken
Driver
mesh network – taken
routing protocols
Logic gate – taken
Deterministic vs. non-deterministic
client
RSSI
DTLS