This article is meant to explain what a VPN is to the layperson with a basic understanding of modern telecommunications in general (how to access the web via a browser, that devices can communicate via the internet) and how to implement a VPN connection for one’s own home network. By the end of the article readers should have the knowledge to explain how a VPN works to someone else and begin implementing a VPN for their home network.
What is a VPN
A Virtual Private Network (VPN) is a networking technology that essentially obfuscates a network user’s IP (Internet Protocol) address to their Internet Service Provider (ISP). An IP address is a numerical label used to uniquely identify a device (like a computer, phone, or printer) connected to a network that uses Internet Protocol (a method of transferring data between machines.) When a computer sends data to another machine across such a network, the data is contained in chunks known as packets. Each packet the computer sends or receives contains the IP address of the sender and the recipient. Thus it is possible for devices through which these packets must travel to get to their destination to determine what two entities are communicating (like a personal computer and a google.com web server.) One such entity is the ISP’s gateway router, which is the organization or company (Comcast, China Telecom) that gives one’s device(s) on their local network the ability to communicate across the public internet.
A VPN is a “private network.” A private network is a network of devices with IP addresses that are only recognizable to other devices within the private network. In order for a device within a private network to communicate with one outside its network, packets must travel through a designated gateway (connection between the private network and the public internet) which will assign the packet a public IP address which is then recognized in the public internet space. A device’s private IP address is not recognizable on the public internet— only its private network’s public IP address is known.
Such a private network is “virtual” in that the connection between a client device and the private network is made across a public network (such as the public internet).
How Does a VPN Work
When a user’s computer is using a VPN service and they type in the url of a website and hit enter, the user’s computer will send encrypted (via one of many types of encryption protocols such as Transport Layer Security (TLS) or Internet Protocol Security (IPsec)) packets to their router and modem, which will send those encrypted packets to their ISP, then on to the VPN server (a server located within the VPN with a private IP specific to this network), where the packets will be decrypted. Then, the decrypted packets will be sent off to the web server corresponding to the IP at the URL the user originally requested. When the packets reach the web server they will be addressed from the public IP of the VPN (rather than the IP that identifies the user’s device), thus telling the website the user just visited that their identity (location, public IP, etc) is that of the VPN rather than their own device (see Fig 1).
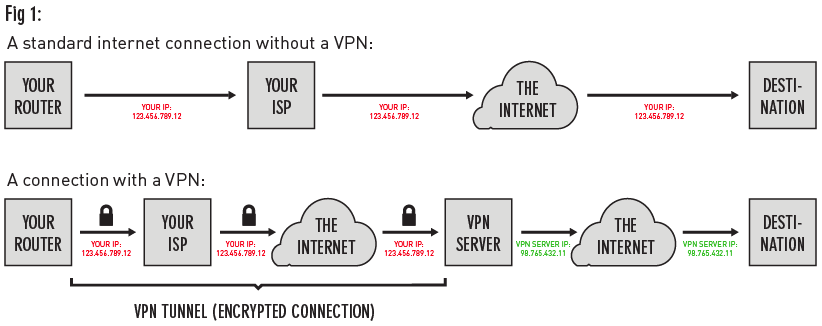
In this transit process packets are encrypted via one of many types of encryption protocols such as Transport Layer Security (TLS) or Internet Protocol Security (IPsec). These protocols make it so that the contents of each packet can only be deciphered by the designated recipient with a specific key, which is administered in a special “handshake” process that occurs between the two devices (like the user’s computer and a web server) right before they transfer data between one another in a way that ensures no middleman can possibly figure out what the key is.
These encryption protocols are used for a variety of purposes on the web and can be implemented without a VPN. What makes a VPN unique is that it extends a private network across a public network (as mentioned earlier). In other words, connecting your machine to a VPN makes your machine part of the private network. This is achieved using a “tunneling protocol.” The encrypted portion of the connection between the user’s computer and the website is the VPN tunnel. Tunneling is the network technology that encrypts all packets (which are also composed, sent, and received based on a given encryption protocol such as TLS or IPSec) sent between the client and the VPN server by a method called “encapsulation”.
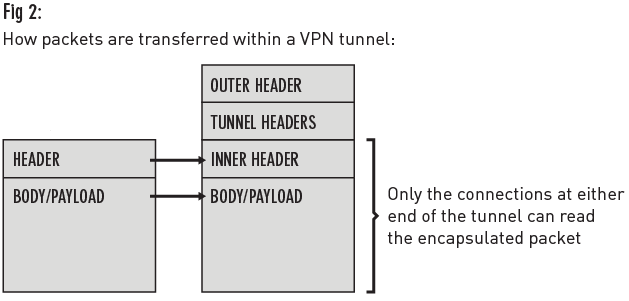
Encapsulation is the process of containing data packets inside packets of a different protocol or IP address space. In the case of a VPN, the packet headers corresponding to the private network IP address space is encapsulated by the headers corresponding to the public IP address space. Each data packet is composed of a “header” and a “payload” (or “body”). The payload is the data to be transferred while the header contains information about the data (such as where it came from and where it’s going). When a packet travels through an IP tunnel, tunnel headers are also added to the packet (over the original packet header), and then another “outer” IP header. These two extra headers render the packets in a format that’s only recognizable between the two devices that opened the tunnel in the first place, thus barring outside interference (see Fig 2).
Tunneling is a method of securing a VPN connection that happens on a different level of the networking infrastructure (known as the Open Systems Interconnection (OSI) model) than the encryption protocols used between the VPN server and the client. There are 7 layers in the OSI model, beginning with layer 1 which describes the physical structure of a telecommunications infrastructure (cables and hubs), moving up to the application layer (layer 7) describing the program the user uses to send, receive, or otherwise access the contents of the data being transferred over the network. Tunneling happens on the network layer (layer 3), which deals with addressing (or figuring out where the data travels over the network). Meanwhile packets travel through the VPN tunnel via an encryption protocol (such as TLS) which spans the higher end of the OSI model above the transport layer (layer 4; but is treated like a transport layer protocol by applications hence being called Transport Layer Security) [1].
Using a VPN
Using a VPN is not a silver bullet for “anonymity” or network safety. Like all tools for anonymity, it’s not guaranteed infallible. It should be used as an additional tool working with other privacy tools, rather than the single solution in itself [2]. It’s up to the user to decide whether a specific thing should be trusted and whether the consequences of the user’s actions are worthwhile; use of a VPN will not absolve the user from being accountable. Since VPN service providers are private companies, they are (in the United States at least) not legally required to disclose what information regarding their customers’ traffic is logged and for how long. If a government entity can prove probable cause for a search and seizure of a customer’s traffic data, and the VPN service has the data, they will be compelled to hand it over to the authorities [3]. In one instance, PureVPN, a VPN service provider, gave law enforcement information about a user who was suspected of cyberstalking. PureVPN stated in their privacy policy that they would share such information if authorities provide appropriate permission [4].
There are countless options when it comes to implementing a VPN connection on a home network. The first decision one should make is whether you should use a VPN service or set up your own server. Choosing to use a VPN service is beneficial to those seeking more of a turnkey operation— less technical understanding, building, and maintenance required. One downside to using a service is that subscriptions often cost money (because running servers and providing the technical means for security and encryption for a number of individuals is not free): anywhere from $3-$15 monthly[5]. The other option is to set up your own VPN server, which has the benefit of potentially lower costs (hardware may need to be purchased if not already owned, along with the ongoing cost of running a server, which can be as low as $5 monthly) as well as more control over server operations.
There are many factors to consider when choosing a VPN service. Of them, reputation, cost, software compatibility, speed, and location, and how up to date the technology is will be covered here. When weighing these factors toward one’s own best interests, it’s important that you do your own research. Part of doing this research means reading the Terms of Service and other fine print that comes with using any service under consideration. Find a VPN service provider with a reputation for being responsible with their traffic. Search their company name on the web and look for articles that talk about them, and read customer reviews. A group of researchers [6] discovered that one popular service called Hola was found to be selling its users’ bandwidth to other users, opening the potential for users’ connections being used for illegal activity without their knowledge. Hola offers a free to use service because, according to the exposé mentioned above, they sell users’ bandwidth to customers of another service called Luminati. This serves as an example of what to look out for when it comes to cost: since these services cost money to provide, where is that money coming from if not advertising or subscription services? Free services should be examined carefully before use. Check the VPN provider’s website to make sure it’s compatible with your device’s operating system from which it will be used, and that it has servers as near to the geographic locations from which the devices will be accessing them most as possible. The further away a VPN server is, the slower the connection speeds may be [7]. Finally, it’s important to make sure the encryption protocol being used in the VPN is up-to-date. Outdated protocols are more likely to contain vulnerabilities that are known to hackers. For example many outdated services use outdated versions of Secure Socket Layer (SSL; now known as TLS: SSLv2 or SSLv3), rather than the current version (TLS 1.2, as of Dec 1 2017.)[8]. Check the official website for the service to determine the protocol(s) being used. If the protocol version used by a VPN service can’t be found, email them and ask.
Considering these factors (low cost but not free, clean reputation, greater global server coverage, higher software compatibility), here are a few top contenders (based on my own research):
As stated before, one’s own research should be done before committing to any service, even the ones listed above. Trusted opinions can be sought from journalists or experts with good reputations, but because there are so many VPN services out there and technology is constantly changing at such a fast pace, it is best to never take anyone else’s word without doing the homework personally.
Setting up a VPN client without using a third-party service can get quite complicated, and is different for whatever hardware and operating system is being used. There are plenty of tutorials online that will walk the user step-by-step through a set-up process specific to their chosen setup. Here are a few:
- How to setup a secure VPN server on Raspberry Pi or DigitalOcean
- Setting up your own VPN with Algo
- How To Set Up an OpenVPN Server on Ubuntu 14.04
In general, setting up one’s own VPN client just means building the interface to connect and send the user’s network data through the remote VPN server. When building such an interface, open source software is recommended primarily due to greater transparency regarding functionality. This software of course must live on a computer, and this computer should be a separate, dedicated machine so that it can be left always on and always connected. Some people choose to use a Raspberry Pi [9], which is a tiny, affordable computer that’s perfect for single-purpose uses like running a VPN connection. Others choose to purchase a subscription to a Virtual Private Server (VPS), which is essentially a computer owned by a third party somewhere else, which can be rented and accessed remotely. One of the cheapest VPS’s available is the $5 monthly instance offered by DigitalOcean, and other popular VPS providers include Amazon Web Services (AWS), Rackspace, and Scaleaway. One of the most known open-source VPN software is OpenVPN. The idea is to have this software running on one of the computers or instances described above, which will make a connection to a remote VPN server to be used by the user’s home network.
As mentioned, setup can get messy. Fortunately there are now plug-and-play solutions being brought forth by the open-source community. Streisand (for BSD, Linux, or macOS) is an all-in-one series of automated tasks that attempts to set up a remote server where it will then install an entire suite of privacy-protection software including OpenVPN that can be executed with just a small series of copy-pasted commands. Another similar option is Algo VPN (macOS, Linux, Windows) which will just install a personal IPSec VPN on a VPS/home server of your choice.
By the time you have a VPN up and running, you should test it to be sure that it’s working. An effective way to determine that a VPN is properly encrypted is to test its connection using tools like the following:
- DNS Leak Test
- Simple IP address test
- Extended IP test (includes details like device and application headers)
- If using a torrent client over VPN, verify that this peer-to-peer activity is not leaking your device info (see “Detected Torrent Address” section)
If these tests result in the identification of your personal device, it’s likely that the VPN connection was not made properly. Otherwise check that you are not using an outdated encryption protocol.
Now you should understand what a private network is, what it means for a private network to be virtual, and what a packet is and how they are secured in a VPN via higher layer encryption protocols and tunneling. Using this knowledge and the provided resources as jumping-off points, you are equipped to confidently begin setting up your own VPN connection and ultimately maintaining the power to remain safe on the public internet.
[1] https://security.stackexchange.com/a/93338 (archived url)
[2] https://arstechnica.com/information-technology/2016/06/aiming-for-anonymity-ars-assesses-the-state-of-vpns-in-2016/ (archived url 1, archived url 2)
[3] https://www.pcworld.com/article/241591/faq_will_your_isp_protect_your_privacy_.html
[4] https://www.theregister.co.uk/2017/10/08/vpn_logs_helped_unmask_alleged_net_stalker_say_feds/ (archived url)
[5] https://www.pcmag.com/article2/0,2817,2403388,00.asp (archived url)
[6] http://adios-hola.org (archived url)
[7] https://support.usenetserver.com/customer/en/portal/articles/2202528-will-using-a-vpn-slow-down-my-internet-speed- (archived url)
[8] https://www.htbridge.com/blog/90-percent-of-ssl-vpns-use-insecure-or-outdated-encryption.html (archived url)
[9] https://blog.hsp.dk/how-to-setup-vpn-server-on-raspberry-pi-or-digitalocean/ (archived url)| https://jacobsalmela.com/2013/08/11/raspberry-pi-and-openvpn-how-to-set-up-openvpn-mac-and-ios-clients/ (archived url)