Email authentication protocols work together to validate your email messages and verify their senders. These protocols help prevent email spoofing and ensure messages come from legitimate sources. Here’s how each protocol works:
Sender Policy Framework (SPF)
SPF validates that the sending mail server is authorized to send emails on behalf of a domain. The receiving email server checks if the sender’s IP address appears in a list of authorized IP addresses published in the domain’s DNS records.
Example:
- Valid: Company ABC sends email from their authorized mail server at IP 1.2.3.4, which is listed in their SPF record
- Invalid: A spammer tries to send email claiming to be from Company ABC but uses an unauthorized server at IP 5.6.7.8
DomainKeys Identified Mail (DKIM)
DKIM adds a digital signature to emails using cryptographic verification. Like a handwritten signature on a check, this mathematical signature proves the email truly came from the claimed domain and hasn’t been tampered with in transit.
Example:
- Valid: An email arrives with a DKIM signature that matches the cryptographic keys published in the sender’s DNS
- Invalid: An attacker tries to modify the content of a signed email, breaking the DKIM signature
Domain-based Message Authentication, Reporting and Conformance (DMARC)
DMARC builds upon SPF and DKIM by verifying that the domain in the “From” header (what users see) matches the domains validated by SPF and DKIM. It also tells receiving servers how to handle emails that fail these checks.
Why DMARC is important: While SPF verifies the sending server and DKIM verifies message integrity, neither ensures that the visible “From” address matches these authenticated domains. For example:
- Sender owns legitdomain.com with valid SPF and DKIM records
- They could send mail using legitdomain.com’s servers and DKIM signatures
- But set the visible “From” address to someone@trusteddomain.com
- Without DMARC, this deceptive email would pass SPF and DKIM checks
- DMARC prevents this by requiring alignment between the visible sender and authenticated domains
Technical Implementation
All three protocols use DNS TXT records to publish their policies. From the receiving server’s perspective:
- DKIM verifies who wrote the email
- SPF verifies which server sent the email
- DMARC validates the visible sender and defines handling of authentication failures
Flowchart
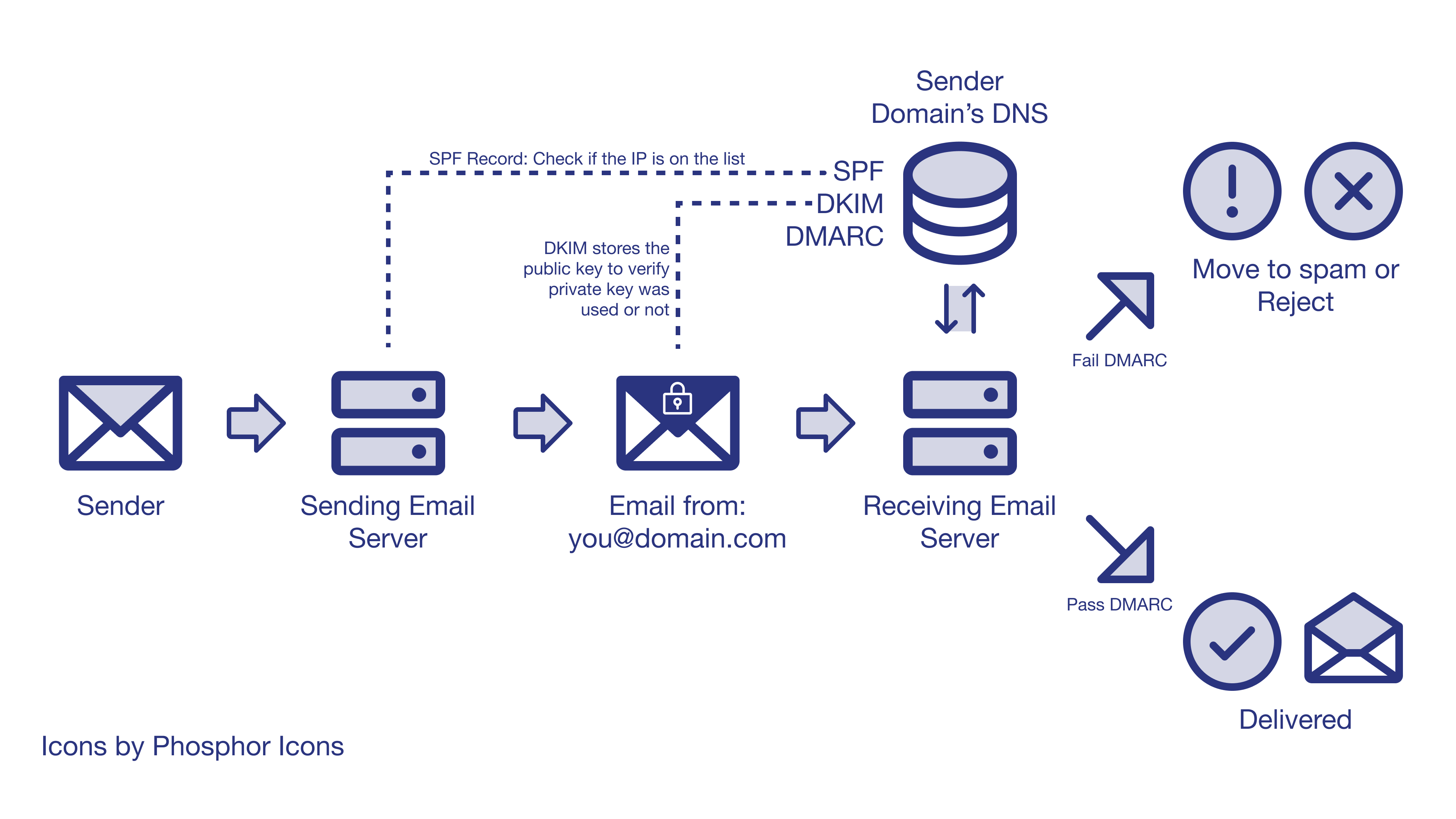
Figure 1. Flow diagram of the relationship between SPF, DKIM and DMARC in email transmission.
Reference
- What are DMARC, DKIM, and SPF? | Cloudflare
- Use DMARC to validate email, setup steps – Microsoft Defender for Office 365 | Microsoft Learn
- SPF, DKIM and DMARC: What are they and how do they work together? | TechTarget
- SPF vs. DKIM vs. DMARC: A Guide | Mimecast
- SPF, DKIM and DMARC: why are they important and how can you set them up?